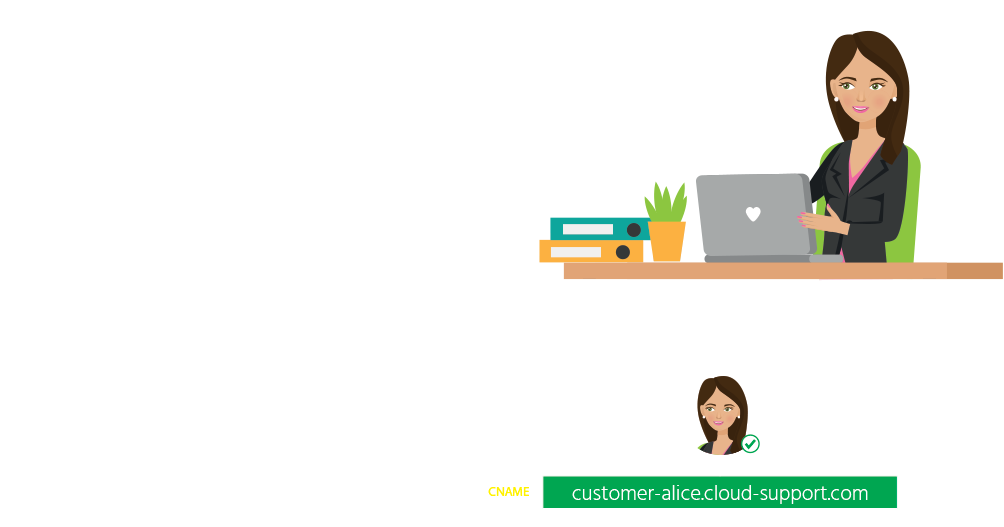
Domain Hijacking is a well-known security issue that can be carried in many different ways. In addition to social engineering or unauthorized access to the...
Search Results For - Cyber
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
Hardentools is a collection of simple utilities designed to disable a number of “features” exposed by operating systems (Microsoft Windows, for now), and...
mitmproxy is your swiss-army knife for debugging, testing, privacy measurements, and penetration testing. It can be used to intercept, inspect, modify and...
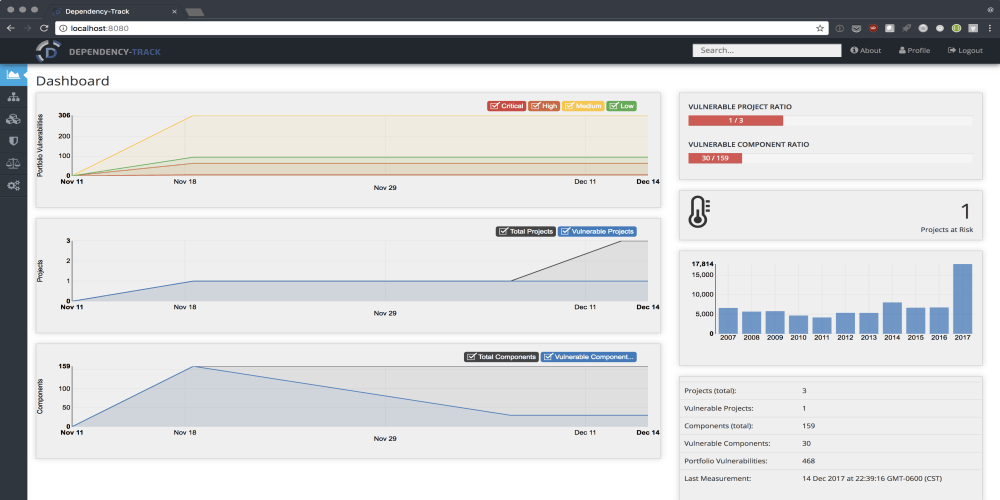
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
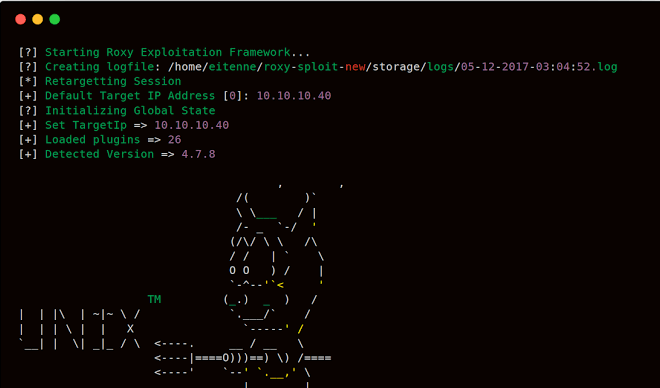
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
The malicious software uncovered pornographic ads and attempted to trick users into buying added services, according to Check Point. “We’ve eliminated the apps...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...