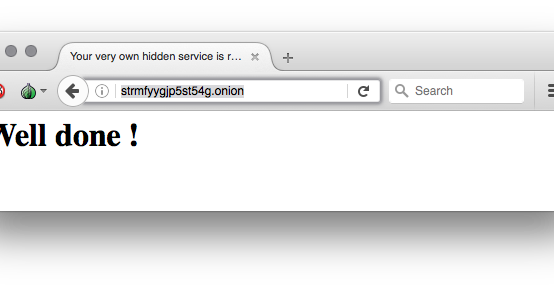
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
Search Results For - Check
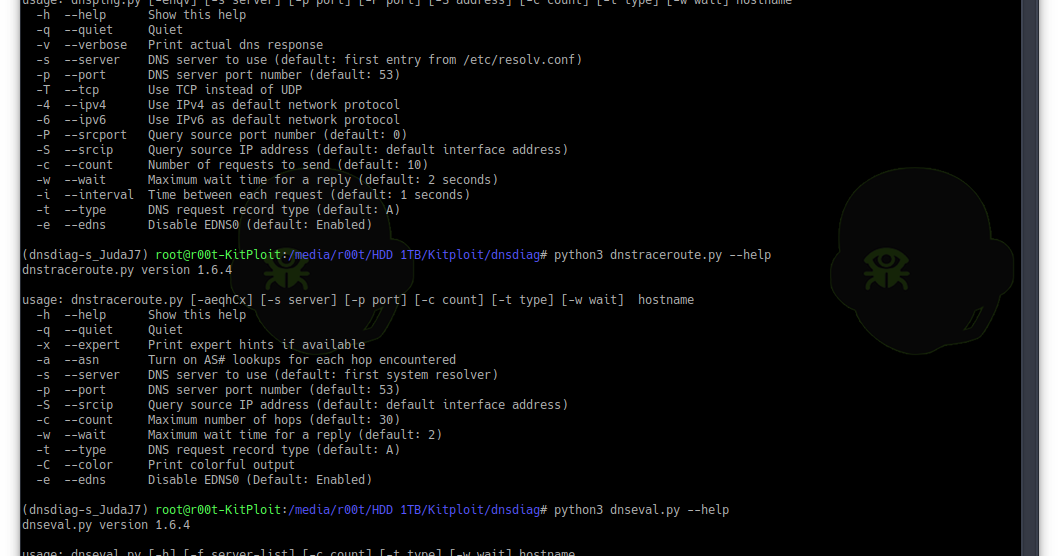
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...
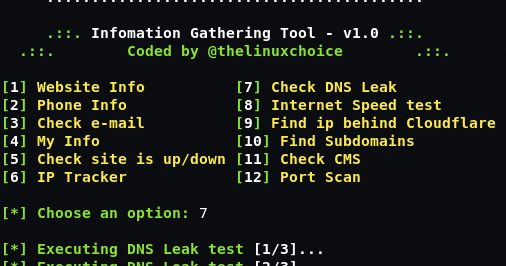
InfoG is a Shellscript to perform Information Gathering. Features Check Website info Check Phone info IP Tracker Check Valid E-mail Check if site is Up/Down...
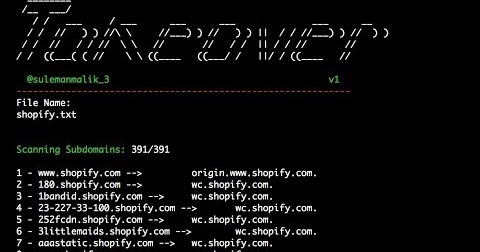
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
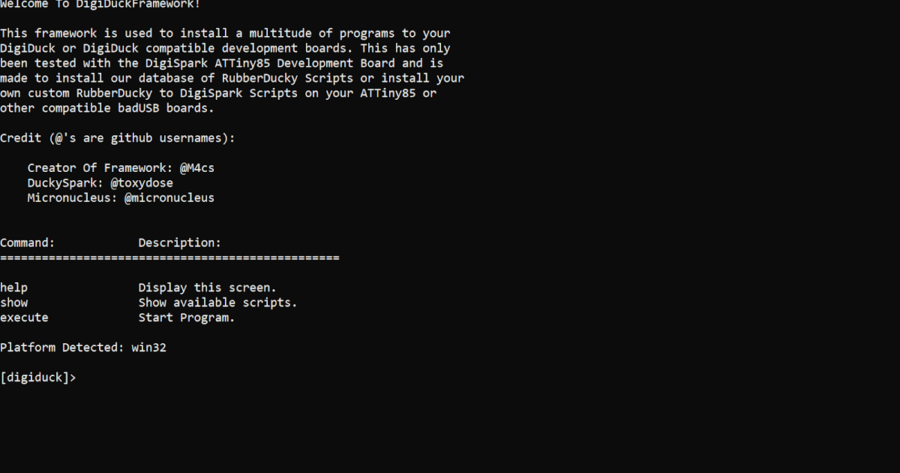
Framework for Digiduck Development Boards running ATTiny85 processors and micronucleus bootloader! Roadmap: Plan to implement a command for Duckyspark...
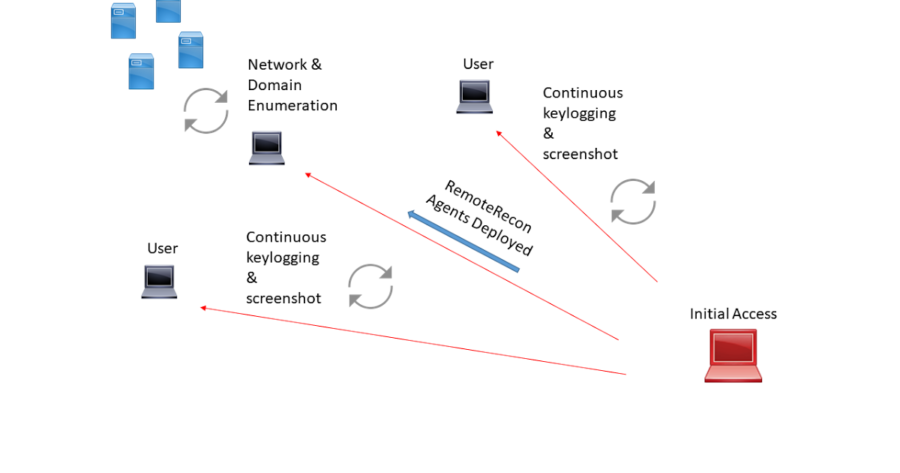
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often...
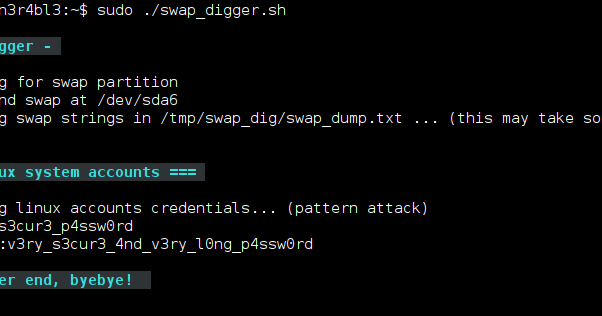
swap_digger is a bash script used to automate Linux swap analysis for post-exploitation or forensics purpose. It automates swap extraction and searches for...
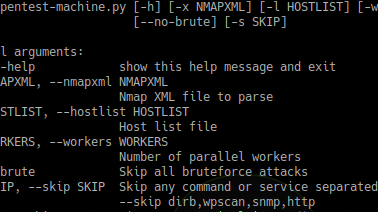
Automates some pentesting work via an nmap XML file. As soon as each command finishes it writes its output to the terminal and the files in output-by-service/...
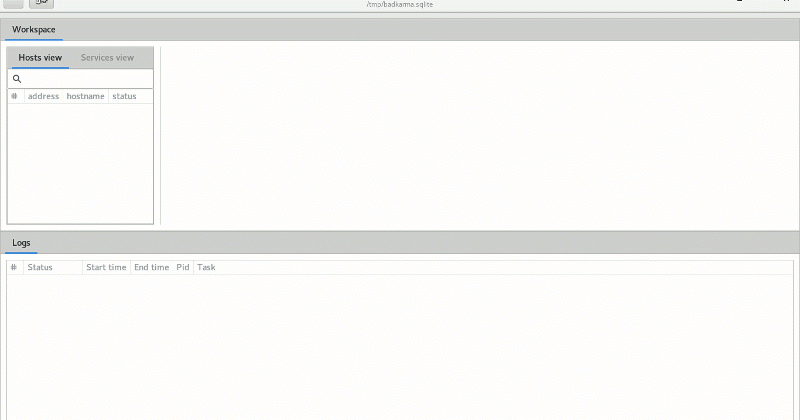
badKarma is a python3 GTK+ network infrastructure penetration testing toolkit. badKarma aim to help the tester in all the penetration testing phases...