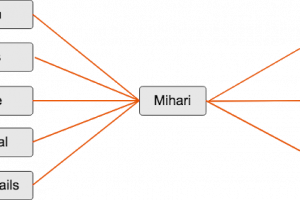
[sc name=”ad_1″] Mihari is a helper to run queries & manage results continuously. Mihari can be used for C2, landing page and phishing hunting...
Search Results For - Check
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
[sc name=”ad_1″] Bpytop, bashtop python port is now available at It’s a lot faster and about a third as cpu heavy and has more features...
[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...
[sc name=”ad_1″] A python based tool for exploiting and managing Android devices via ADB Currently on development Screenrecord Stream Screenrecord...
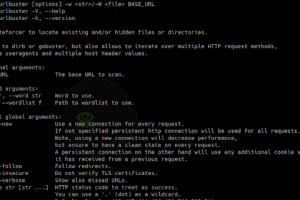
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
[sc name=”ad_1″] By @s0lst1c3 Disclaimer DropEngine (the “Software”) and associated documentation is provided “AS IS”. The Developer...
[sc name=”ad_1″] ReconSpider is most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations...