DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
Search Results For - C2
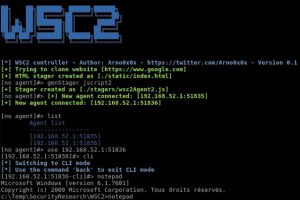
WSC2 is a PoC of using the WebSockets and a browser process to serve as a C2 communication channel between an agent, running on the target system, and a...
TrevorC2 is a client/server model for masking command and control through a normally browsable website. Detection becomes much harder as time intervals are...
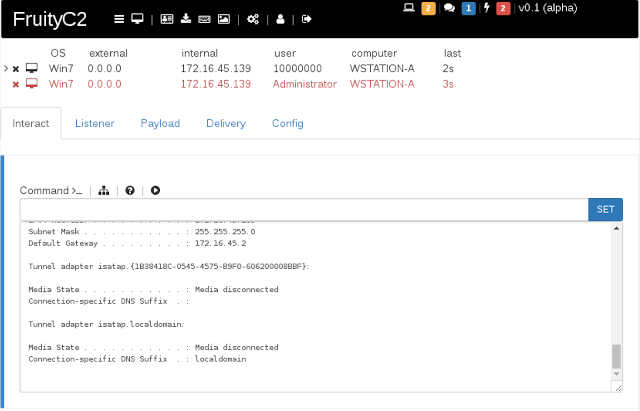
This is the initial release for FruityC2 (alpha version). Can be installed on any linux system, but the installation scripts are made for Debian based systems...
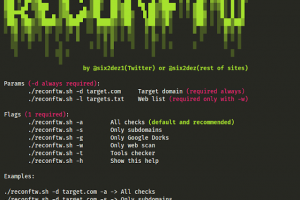
[sc name=”ad_1″] This is a simple script intended to perform a full recon on an objective with multiple subdomains tl;dr Requires Go Run ./install...
[sc name=”ad_1″] HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims on the detection of...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] The all-in-one Red Team browser extension for Web Pentesters HackTools, is a web extension facilitating your web application...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] This is a tool that allows you to offensively use YARA to apply a filter to the events being reported by windows event logging...