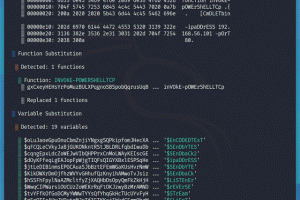
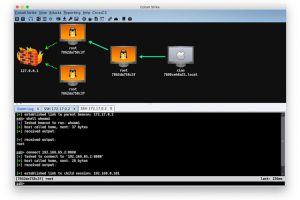
Hey Guys, In this video i show you how to generate shellcodes and Backdoors using ShellSploit Framework and Kali Linux 2017.2. ShellSploit: Shellsploit...
Search Results For - Backdoor
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] drow is a command-line utility that is used to inject code and hook the entrypoint of ELF executables (post-build). It takes...
[sc name=”ad_1″] Chimera is a (shiny and very hack-ish) PowerShell obfuscation script designed to bypass AMSI and antivirus solutions. It digests...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
[sc name=”ad_1″] A python based tool for exploiting and managing Android devices via ADB Currently on development Screenrecord Stream Screenrecord...
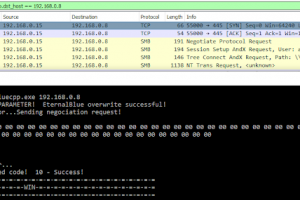
[sc name=”ad_1″] EternalBlue suite remade in C which includes: MS17-010 Exploit, EternalBlue/MS17-010 vulnerability detector, DoublePulsar detector...
[sc name=”ad_1″] Bramble software has been designed for the bramble project. It incorporates many features of pentesting and IT Security...
[sc name=”ad_1″] Port forwarding or port mapping is an application of network address translation that redirects a communication request from one...