[sc name=”ad_1″] Blog can be found at Script made for all your javascript recon automation in bugbounty. Just pass subdomain list to it and options...
Search Results For - Automation
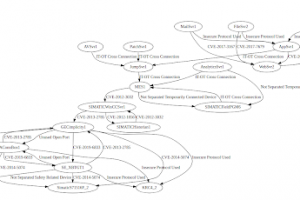
[sc name=”ad_1″] This prototype identifies security risk sources (i.e., threats and vulnerabilities) and types of attack consequences based on...
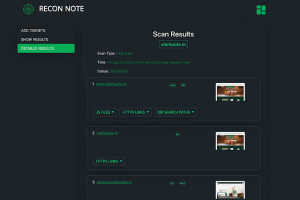
[sc name=”ad_1″] Web Application Security Recon Automation Framework It takes user input as a domain name and maximize the attack surface area by...
[sc name=”ad_1″] A security researcher has discovered a severe vulnerability in the popular, open source event-driven platform StackStorm that...
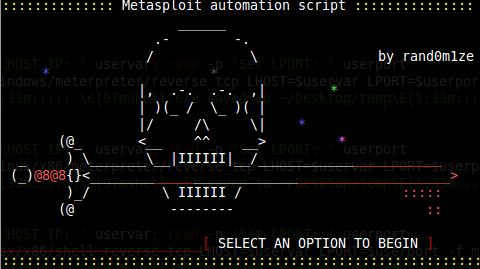
Command line script for automating metasploit functions: Checks for metasploit service and starts if not present Easily craft meterpreter reverse_tcp...
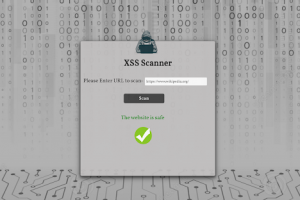
[sc name=”ad_1″] Cross-Site Scripting (XSS) is one of the most well known web application vulnerabilities. It even has a dedicated chapter in the...
[sc name=”ad_1″] Although 2020 has been the worst year since 1945, as last year, this year we made a ranking with the most popular tools between...
[sc name=”ad_1″] Project Bheem is a simple collection of small bash-scripts which runs iteratively to carry out various tools and recon process...
[sc name=”ad_1″] A collection of proof-of-concept source code and scripts for executing remote commands over WinRM using the WSMan.Automation COM...
[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...