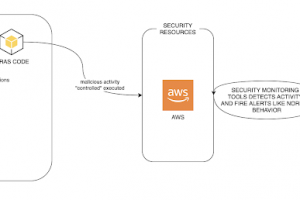
[sc name=”ad_1″] Security Incident Response Automated Simulations (SIRAS) are internal/controlled actions that provide a structured opportunity to...
Search Results For - Automation
[sc name=”ad_1″] An automation tool that scans sub-domains, sub-domain takeover and then filters out xss, ssti, ssrf and more injection point...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] Linux evil toolkit is a framework that aims to centralize, standardize and simplify the use of various security tools for pentest...
[sc name=”ad_1″] Scripthunter is a tool that finds javascript files for a given website. To scan Google, simply run ./scripthunter.sh . Note that...
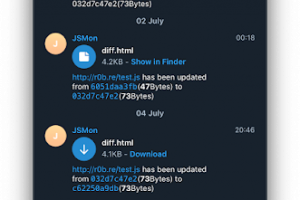
[sc name=”ad_1″] Using this script, you can configure a number of JavaScript files on websites that you want to monitor. Everytime you run this...
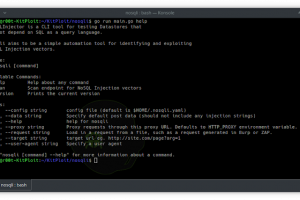
[sc name=”ad_1″] NoSQL scanner and injector. About Nosqli I wanted a better nosql injection tool that was simple to use, fully command line based...
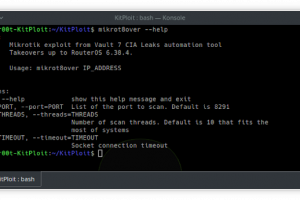
[sc name=”ad_1″] mikrot8over: Fast exploitation tool for Mikrotik RouterOS up to 6.38.4 This is reworked original Mikrotik Exploit. Added Python 2...
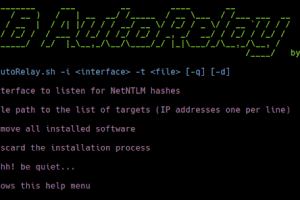
[sc name=”ad_1″] SMB AutoRelay provides the automation of SMB/NTLM Relay technique for pentesting and red teaming exercises in active directory...
[sc name=”ad_1″] Welcome to the Microsoft Defender Advanced Threat Protection PowerShell module! This module is a collection of easy-to-use cmdlets...