Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
Search Results For - Audit
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
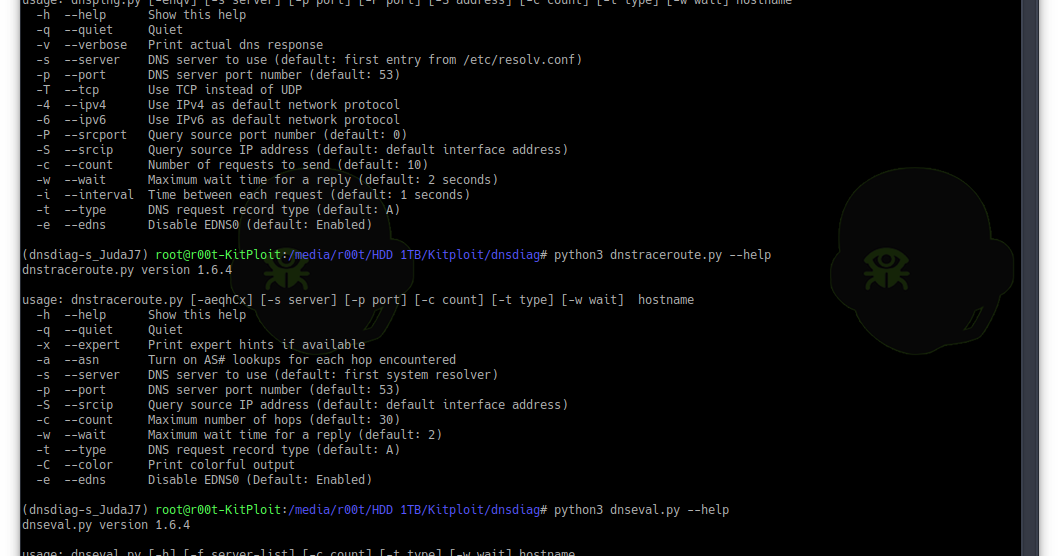
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...
Security Monkey monitors your AWS and GCP accounts for policy changes and alerts on insecure configurations. Support is available for OpenStack public and...
Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...
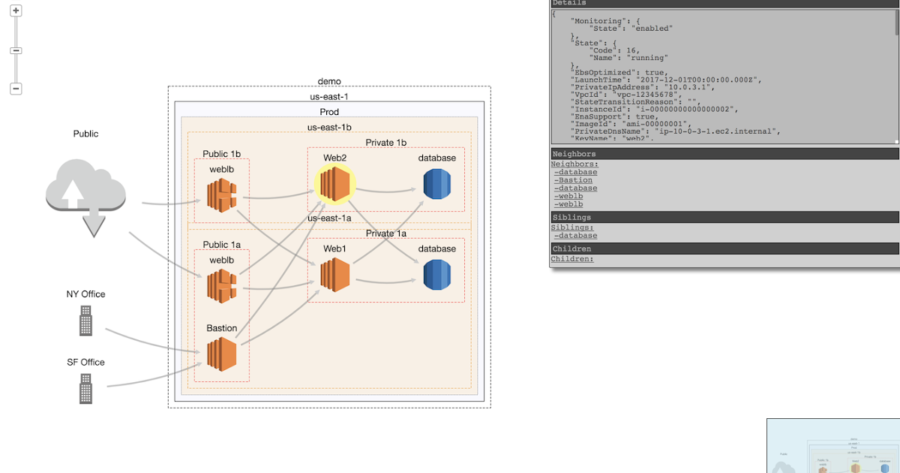
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...
GlobaLeaks is open-source / free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
Sn1per Community Edition is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Sn1per...
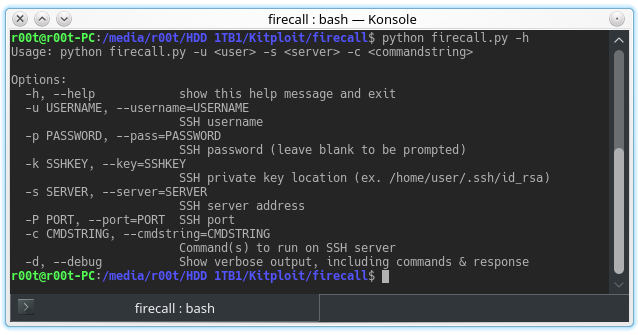
Automate SSH communication with firewalls, switches, etc. Description These scripts are designed to automate sending commands to a Cisco ASA firewall. The...