[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
Search Results For - Audio
[sc name=”ad_1″] If you own an Apple device, you should immediately turn OFF FaceTime app for a few days. A jaw-dropping unpatched privacy bug has...
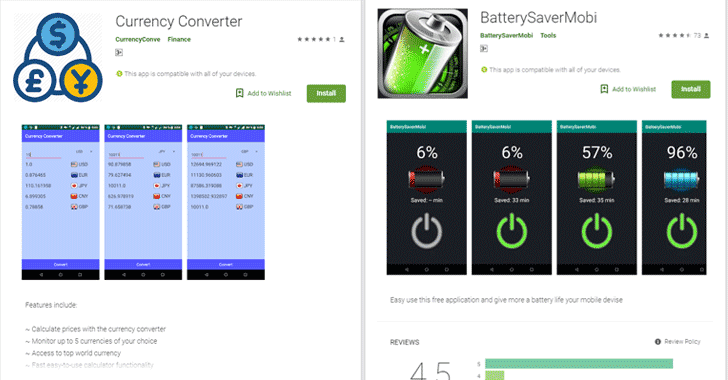
[sc name=”ad_1″] Even after so many efforts by Google for preventing its Play Store from malware, shady apps somehow managed to fool its anti...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
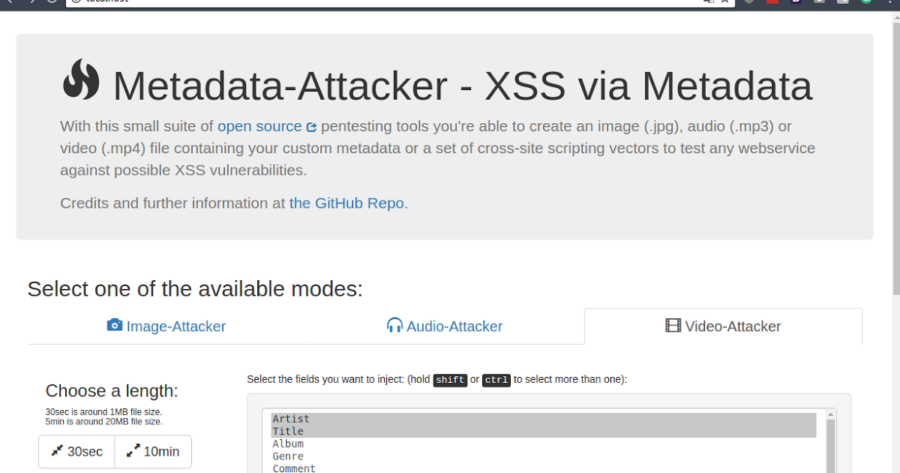
Metadata-Attacker or a set of cross-site scripting vectors to test any webservice against possible XSS vulnerabilities when displaying unfiltered meta datWith...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
SDRtrunk is an integrated application for demodulating radio signals and decoding trunked radio network protocols and some related radio signal formats. The...
Alphonso, a startup that retails media-viewing data, provides a plugin that listens for audio signals in shows and movies. Approximately 250 mobile...
The keylogging code was embedded in the SynTP.sys file, which is a module of the Synaptics Touchpad driver that ships with HP notebook models. “The logging was...
Reptile is a LKM rootkit for evil purposes. If you are searching stuff only for study purposes, see the demonstration codes. Features Give root to unprivileged...