The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
Search Results For - Antivirus
MoneyTaker hackers, A group of Russian hackers, has been laying waste to banks internationally and locally. In the past 18 months, this group has stolen a...
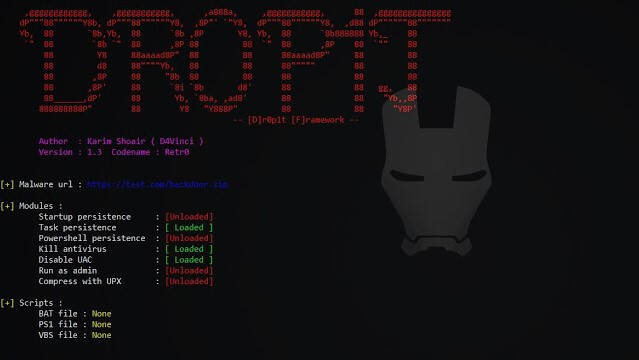
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
Google’s new Play Protect security system did not success first real-world tests, and the system was rated dead in an experiment conducted by independent...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
Habu is to teach (and learn) some concepts about Python and Network Hacking. These are basic functions that help with some tasks for Ethical Hacking and...
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...