The motion seeks to make it more stressful for students to cheat in exams. As a section of the new rules, schools will also be allotted to do history checks on...
Search Results For - Access
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
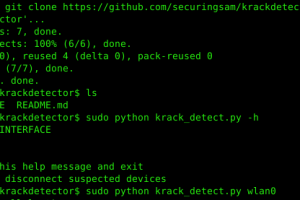
KRACK Detector is a Python script to detect possible KRACK attacks against client devices on your network. The script is meant to be run on the Access Point...
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on...
Many internet giants offer security measures like two-factor authentication (which you should really use) to keep your account safe from hackers. But there are...
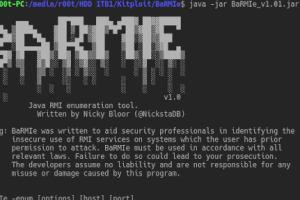
BaRMIe is a tool for enumerating and attacking Java RMI (Remote Method Invocation) services. RMI services often expose dangerous functionality without adequate...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
Unfortunately, it looks like the method is still in effect. Philip Neustrom, the co-founder of Shotwell Labs, lately found two demo websites that would pass...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...