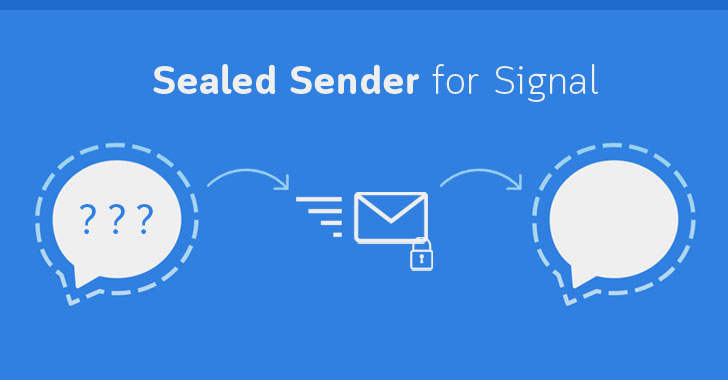
Signal, the popular end-to-end encrypted messaging app, is planning to roll out a new feature that aims to hide the sender’s identity from potential...
Search Results For - Access
Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
Late last month Facebook announced its worst-ever security breach that allowed an unknown group of hackers to steal secret access tokens for millions of...
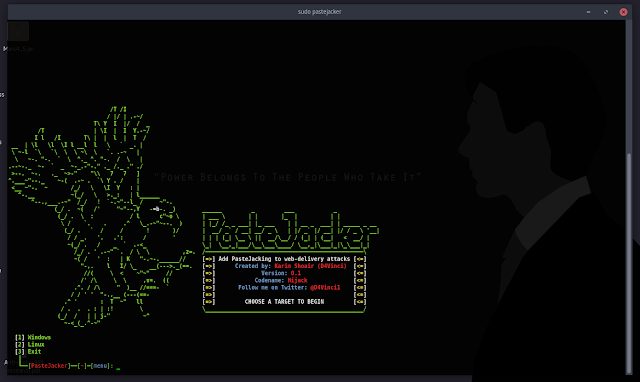
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract...
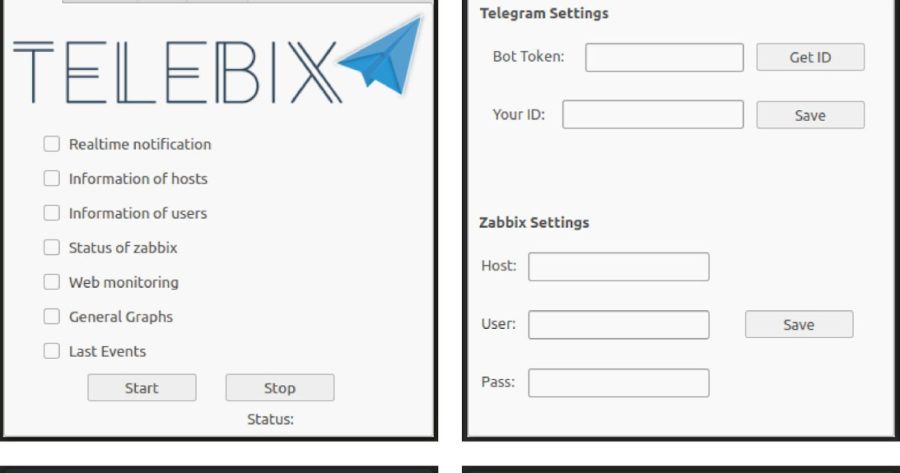
Telebix is an application that communicates with a Bot on the Telegram to receive commands and send information from an infrastructure monitored by Zabbix...
Facebook has finally been slapped with its first fine of £500,000 for allowing political consultancy firm Cambridge Analytica to improperly gather and...
Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
Injects C# EXE or DLL Assembly into any CLR runtime and AppDomain of another process. The injected assembly can then access static instances of the injectee...