A security enthusiast who discovered a passcode bypass vulnerability in Apple’s iOS 12 late last month has now dropped another passcode bypass bug that...
Search Results For - Access
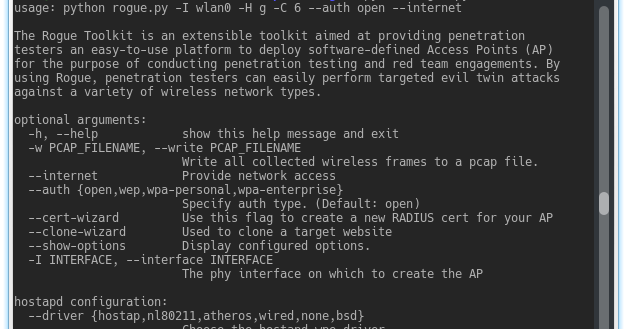
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP)...
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP) for the...
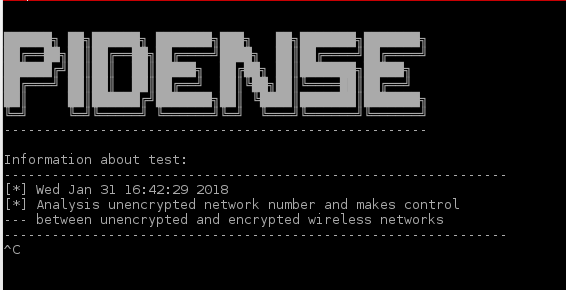
Monitor illegal wireless network activities. Similar SSID broadcasts Same SSID broadcasts Calculates unencrypted wireless networks density Watches SSID...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
Just over a month after OnePlus was caught collecting personally identifiable information on its users, the Chinese smartphone company has been found leaving a...
Apple’s privacy signs do not spread to the thousands of app developers who will gain access to facial data in order to increase entertainment features for...
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
[sc name=”ad_1″] A tool to hunt for credentials in the GitHub wild AKA git*hunt Getting started Install the tool Configure your GitHub token Search...
[sc name=”ad_1″] HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims on the detection of...