[sc name=”ad_1″] A graphical interface to use information security tools by the browser. Getting Started Kali Linux Tools Interface is a graphical...
Search Results For - /Secure
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...
[sc name=”ad_1″] Threat Dragon is a free, open-source, cross-platform threat modeling application including system diagramming and a rule engine to...
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...
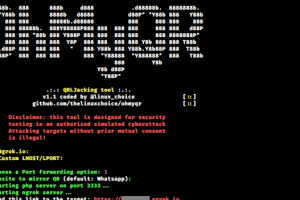
[sc name=”ad_1″] QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking...
[sc name=”ad_1″] Exegol is a fully configured kali light base with a few useful additional tools (~50), a few useful resources (scripts and...
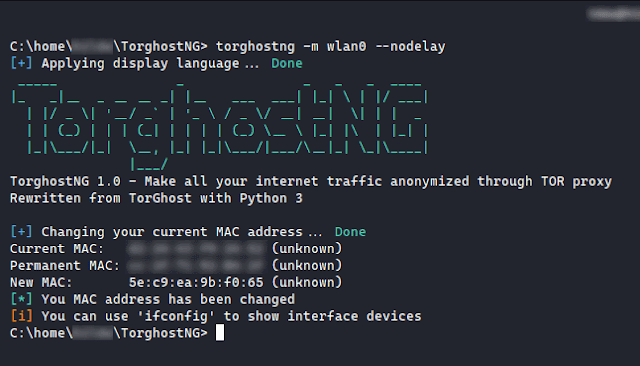
[sc name=”ad_1″] TorghostNG is a tool that make all your internet traffic anonymized through Tor network. Rewritten from TorGhost with Python 3...
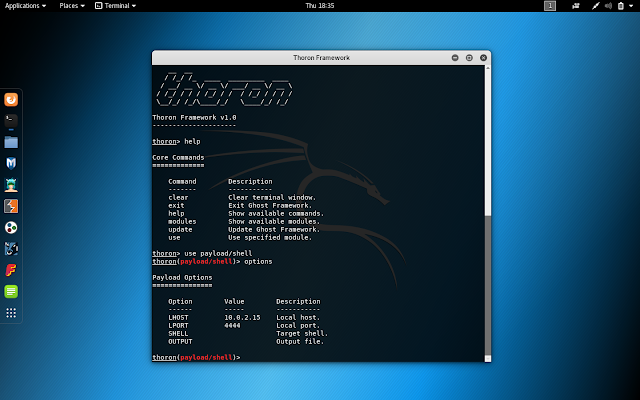
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
[sc name=”ad_1″] Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and...
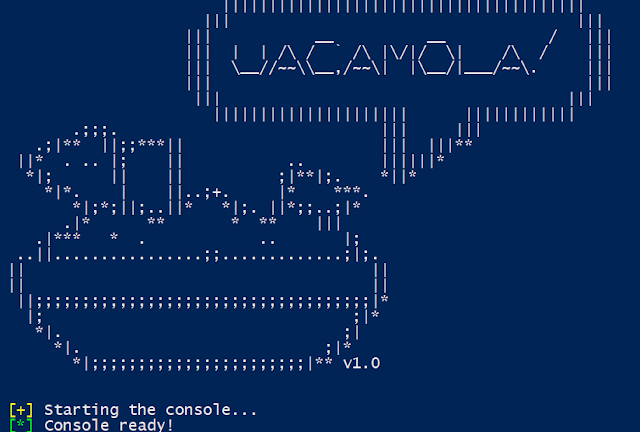
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...