[sc name=”ad_1″] Background A while back I was challenged to write a discovery tool with Python3 that could automate the process of finding...
Search Results For - /Secure
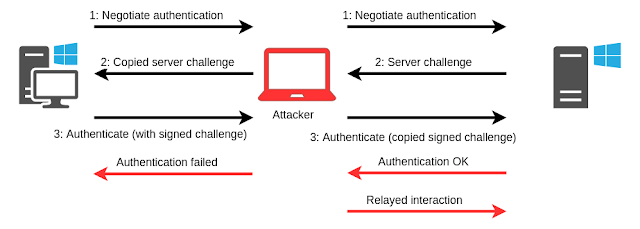
[sc name=”ad_1″] POC tools accompanying the blog Abusing Exchange: One API call away from Domain Admin. Requirements These tools require impacket...
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a Digital Forensics project. Currently, the project...
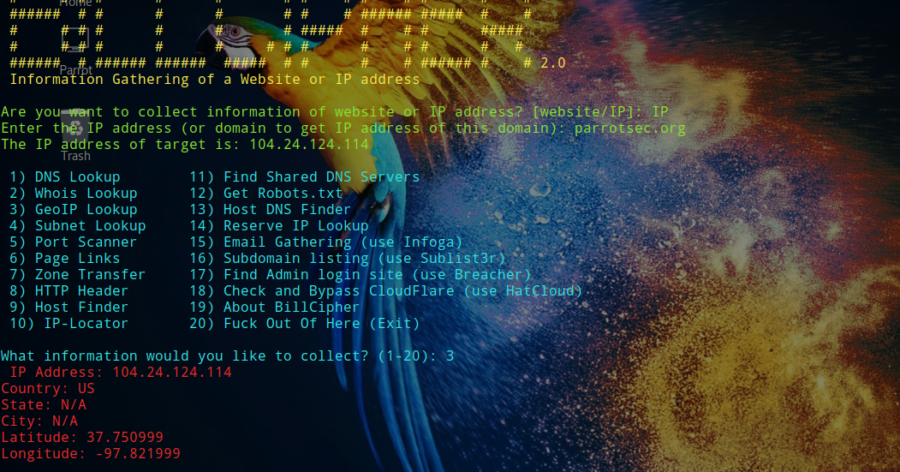
Information Gathering tool for a Website or IP address, use some ideas from Devploit. BillCipher can work in any operating system if they have and support...
GlobaLeaks is open-source / free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
Kali Linux 2018.1 the first release of 2018, this fine release contains all updated packages and bug fixes since our 2017.3 release last November. This release...
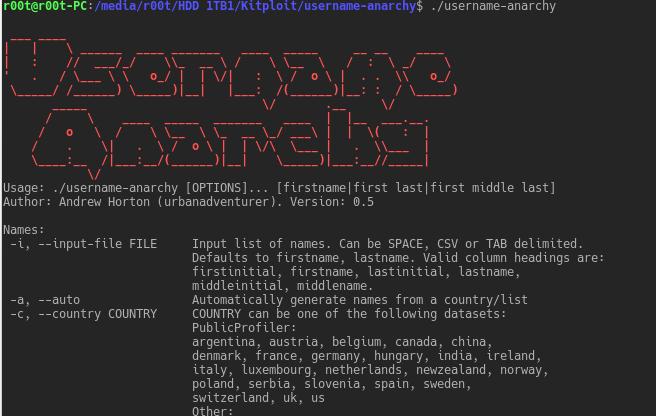
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...
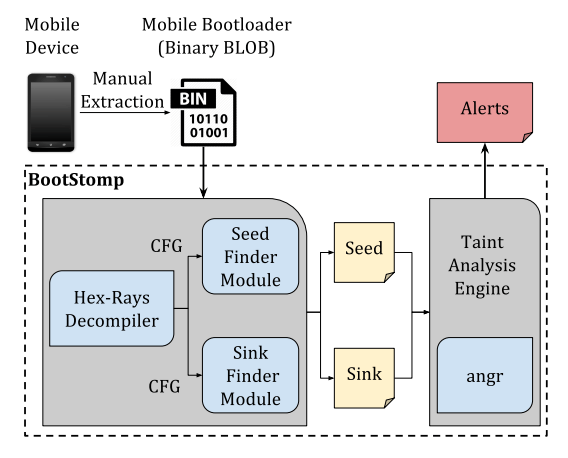
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
In May 2017, Kaspersky security researchers have noticed a forum post advertising ATM (Automated teller machine) malware that was targeting specific vendor...