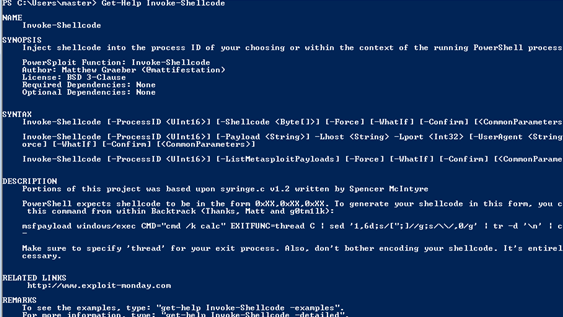
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
Search Results For - /Credentials
[sc name=”ad_1″] SkyWrapper is an open-source project which analyzes behaviors of temporary tokens created in a given AWS account. The tool is...
[sc name=”ad_1″] Integration of Clair and Docker Registry (supports both Clair API v1 and v3) Klar is a simple tool to analyze images stored in a...
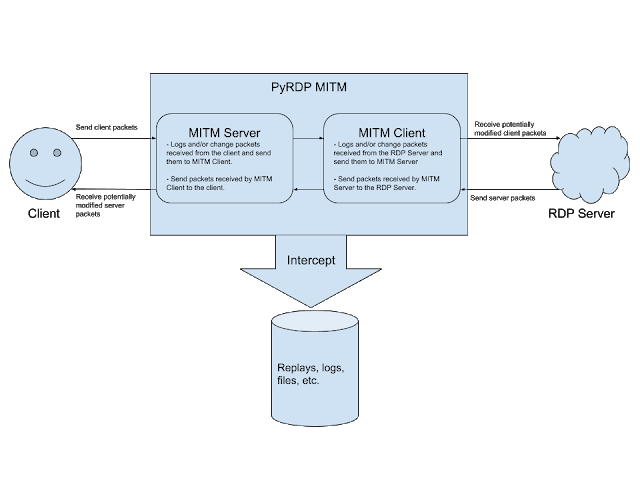
[sc name=”ad_1″] PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library. It features a few tools: RDP Man-in-the...
[sc name=”ad_1″] by Gabriel Ryan (s0lst1c3)(gryan[at]specterops.io) EAPHammer is a toolkit for performing targeted evil twin attacks against WPA2...
[sc name=”ad_1″] Anteater is an open framework to prevent the unwanted merging of nominated strings, filenames, binaries, depreciated functions...
[sc name=”ad_1″] Scout Suite is an open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments...
[sc name=”ad_1″] Phishing Simulation mainly aims to increase phishing awareness by providing an intuitive tutorial and customized assessment...
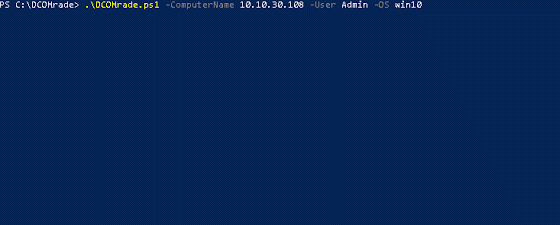
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...
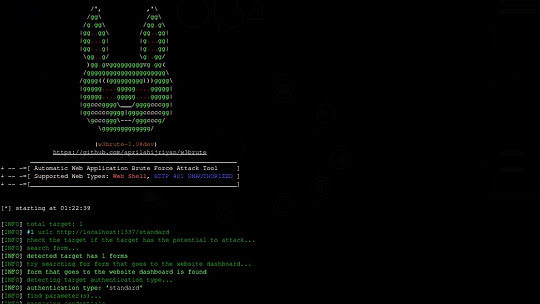
w3brute is an open source penetration testing tool that automates attacks directly to the website’s login page. w3brute is also supported for carrying...