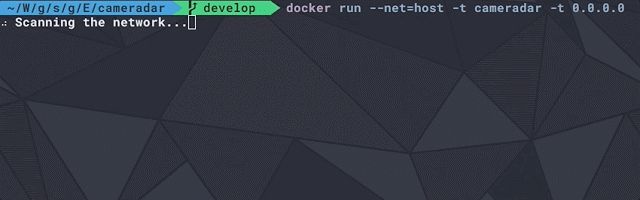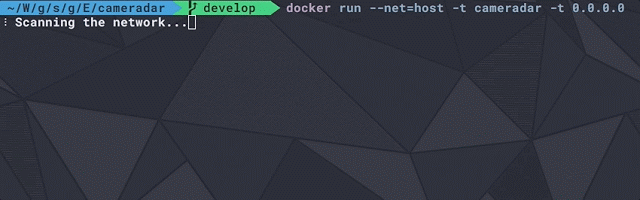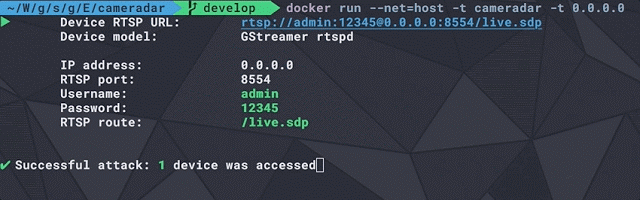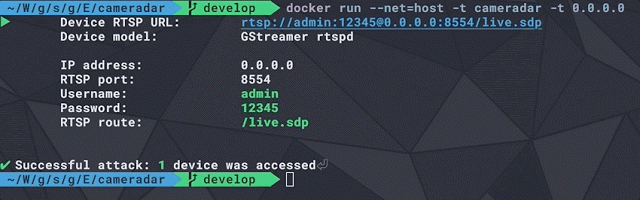
[sc name=”ad_1″] An RTSP stream access tool that comes with its library Cameradar allows you to Detect open RTSP hosts on any accessible target...
Search Results For - /Credentials
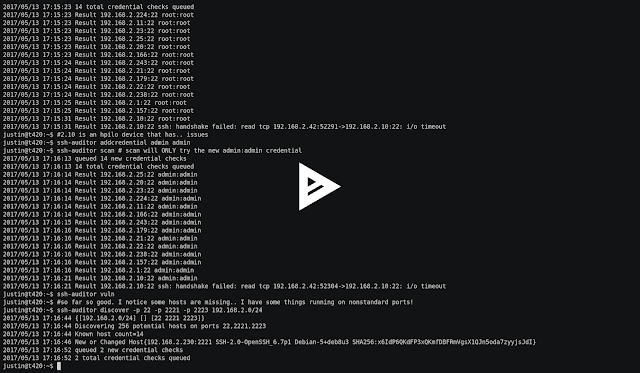
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...
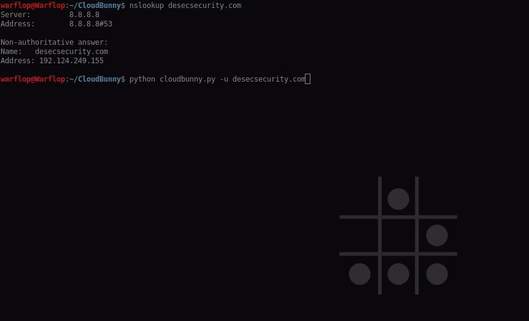
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
This tool allows you to perform OSINT and reconnaissance on an organisation or an individual. It allows one to search 1.4 Billion clear text credentials which...
Console Application designed to interact with SharpSploit released by @cobbr_io SharpSploit is a tool written by @cobbr_io that combines many techniques/C#...
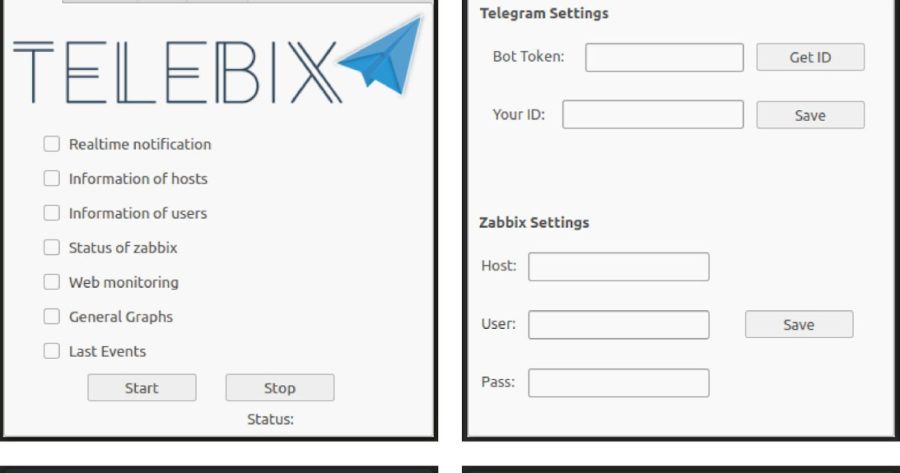
Telebix is an application that communicates with a Bot on the Telegram to receive commands and send information from an infrastructure monitored by Zabbix...
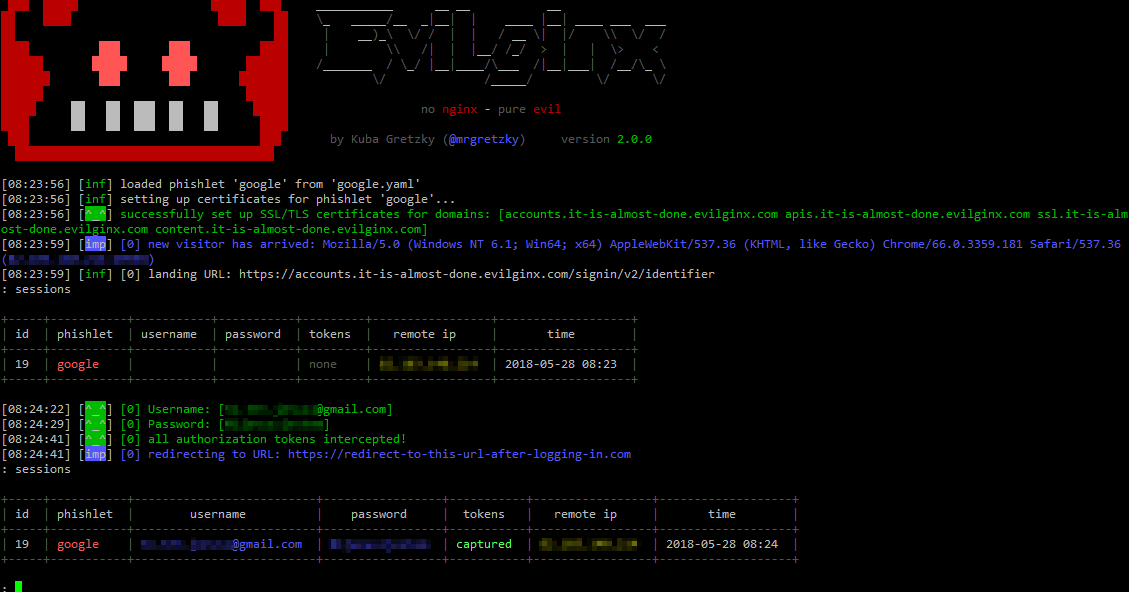
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor...
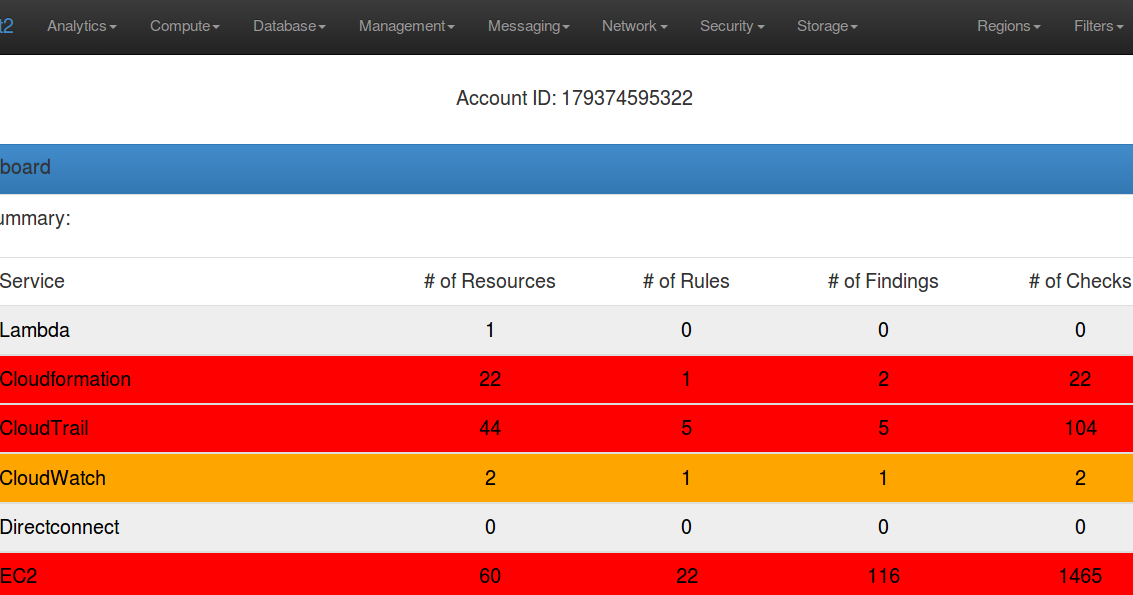
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
Security Monkey monitors your AWS and GCP accounts for policy changes and alerts on insecure configurations. Support is available for OpenStack public and...
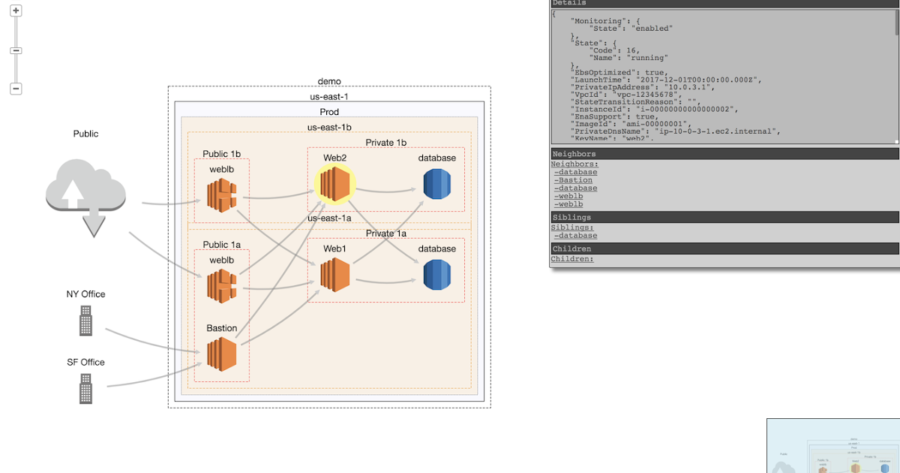
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...