Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to achieve...
A dark web drugs kingpin who was arrested last year when he arrived in the United States to compete in the World Beard and Mustache Championships has now been sentenced...
Late last month Facebook announced its worst-ever security breach that allowed an unknown group of hackers to steal secret access tokens for millions of accounts by...
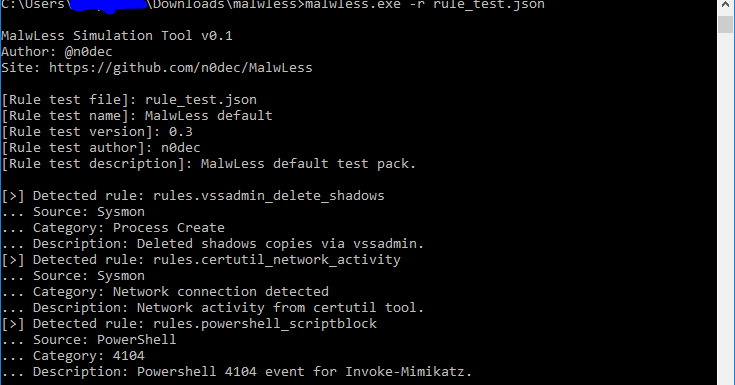
MalwLess is an open source tool that allows you to simulate system compromise or attack behaviours without running processes or PoCs. The tool is designed to test Blue...
Yes, it is official. The massively popular battle royale video game from Epic Games, Fortnite: Battle Royale is finally available for Android devices. Epic announced...
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its other...
Cybersecurity researchers have revealed an unpatched logical flaw in Microsoft Office 2016 and older versions that could allow an attacker to embed malicious code inside...
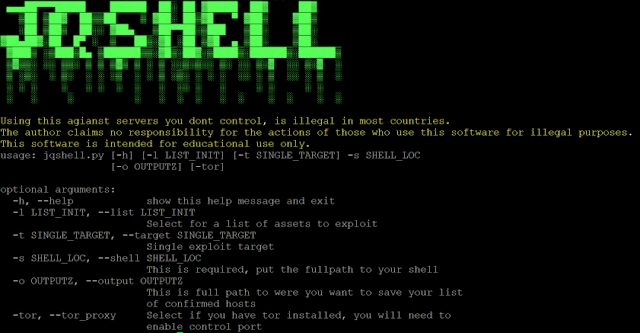
JQShell A weaponized version of CVE-2018-9206 (Unauthenticated arbitrary file upload vulnerability in Blueimp jQuery-File-Upload <= v9.22.0). Disclaimer Using this...
It’s been quite a year for the open source platforms. Earlier this year, Microsoft acquired popular code repository hosting service GitHub for $7.5 billion, and...
Microsoft Windows built-in anti-malware tool, Windows Defender, has become the very first antivirus software to have the ability to run inside a sandbox environment...