[sc name=”ad_1″] Automated Web Assets Enumeration & Scanning Instructions for running Create an account on Zulip Navigate to Settings >...
[sc name=”ad_1″] GRecon (Greei-Conn) is a simple python tool that automates the process of Google Based Recon AKA Google Dorking The current Version 1.0 Run...
[sc name=”ad_1″] 0d1n is a tool for automating customized attacks against web applications. This tool is very faster because uses thread pool and C language...
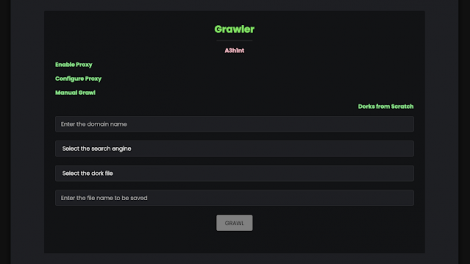
[sc name=”ad_1″] Grawler is a tool written in PHP which comes with a web interface that automates the task of using google dorks, scrapes the results, and...
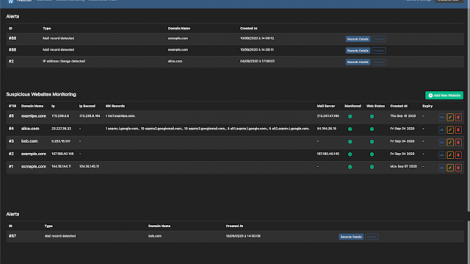
[sc name=”ad_1″] Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your organisation. It...
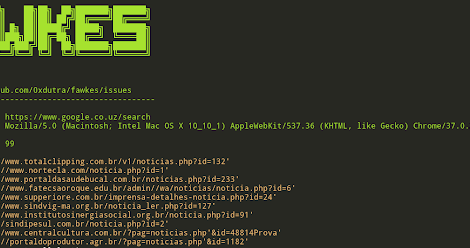
[sc name=”ad_1″] Fawkes is a tool to search for targets vulnerable to SQL Injection. Performs the search using Google search engine. Options -q, ...
[sc name=”ad_1″] Sploit is a Go package that aids in binary analysis and exploitation. The motivating factor behind the development of sploit is to be able...
[sc name=”ad_1″] Project Bheem is a simple collection of small bash-scripts which runs iteratively to carry out various tools and recon process & store...
[sc name=”ad_1″] A bento (弁当, bentō) is a single-portion take-out or home-packed meal of Japanese origin. Bento Toolkit is a simple and minimal docker...
[sc name=”ad_1″] Information Gathering Tool – Dns/Subdomain/Port Enumeration Installation First of all, clone the repo locally git clone Scilla has...