[sc name=”ad_1″] A Modular Penetration Testing Framework Install pip install fsociety Update pip install --upgrade fsociety Usage usage: fsociety [-h] [-i] [...
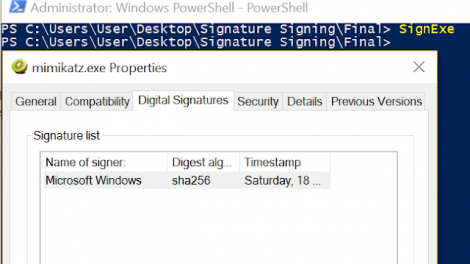
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell code and...
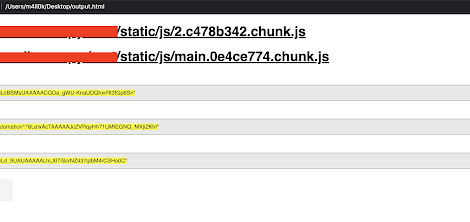
[sc name=”ad_1″] SecretFinder is a python script based on LinkFinder, written to discover sensitive data like apikeys, accesstoken, authorizations, jwt,..etc...
Introduction Docker is an application that simplifies the process of managing application processes in containers. Containers let you run your applications in resource...
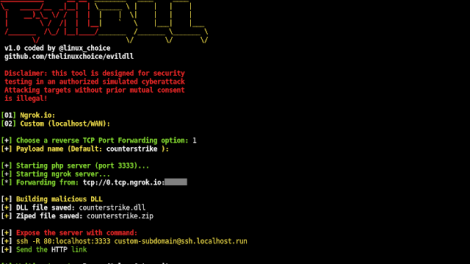
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features: Reverse TCP...
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right now is...
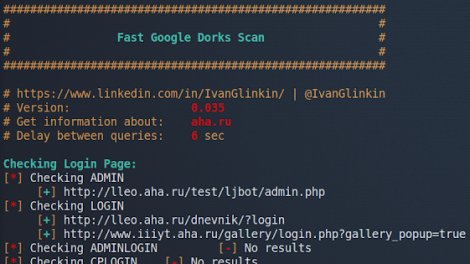
[sc name=”ad_1″] A script to enumerate web-sites using Google dorks. Usage example: ./FGDS.sh megacorp.one Version: 0.035, June 07, 2020 Features: Looking...
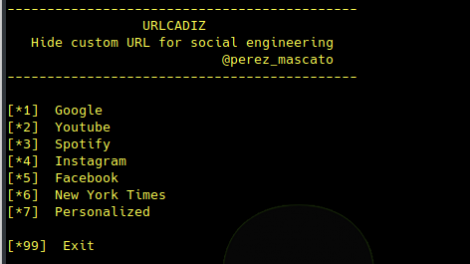
[sc name=”ad_1″] A simple script to generate a hidden url for social engineering. Legal disclaimer: Usage of URLCADIZ for attacking targets without prior...
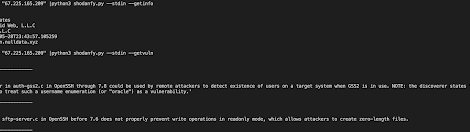
[sc name=”ad_1″] Get ports,vulnerabilities,informations,banners,..etc for any IP with Shodan (no apikey! no rate limit!) Usage # python3 shodanfy.py...
[sc name=”ad_1″] KeyLogger for Linux Systems. Features Runs on GUI systems or CLI Sending data by email Dependencies curl libx11-dev (Debian-Based) libX11...