Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as well as...
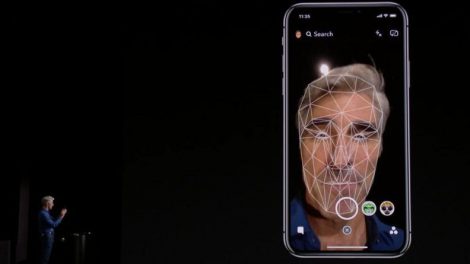
Apple uses the Tenth Anniversary iPhone X Phone to replace Touch ID. Because the award handset features an edge-to-edge protection and has very slim bezels, Apple had to...
Bitcoin surged on Monday, recovering more than $1,000 after losing almost a third of its value in less than four days as traders bought back into the volatile...
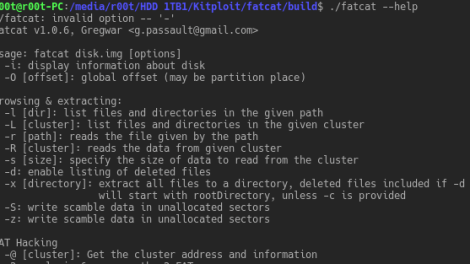
This tool is designed to manipulate FAT filesystems, in order to explore, extract, repair, recover and forensic them. It currently supports FAT12, FAT16 and FAT32...
News of the event was posted on Twitter by vigilante hacker, “The Jester,” who has in the past increased fame by hacking jihadist websites, and who in October 2016...
Blockchain.info is a bitcoin cryptocurrency wallet and block explorer service. Started in August 2011, the service presents information on new transactions, mined blocks...
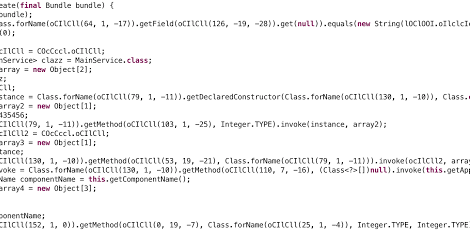
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify. Before...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year-long...
TrevorC2 is a client/server model for masking command and control through a normally browsable website. Detection becomes much harder as time intervals are different and...
The tool itself is impressive enough, serving as the backbone of the CIA’s malware processes, but there’s more. What’s interesting about the first leak in the Vault 8...