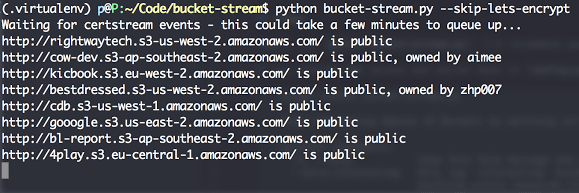
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and audit...
A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later stolen by...
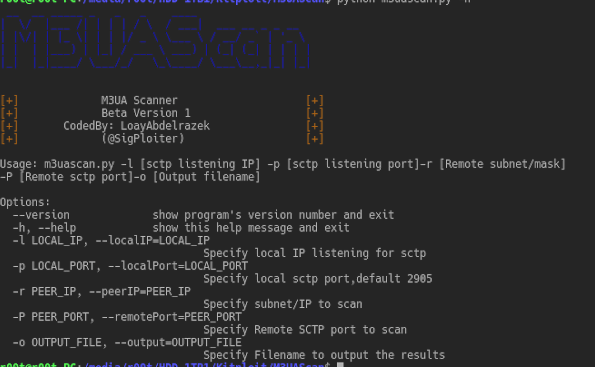
A Scanner for M3UA protocol to detect Sigtran supporting nodes M3UA stands for MTP Level 3 (MTP3) User Adaptation Layer as defined by the IETF SIGTRAN working group in...
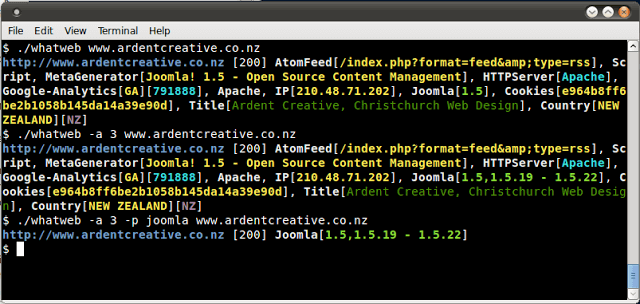
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management systems (CMS)...
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the email and...
After rapidly reinforcing a flaw that acknowledged anyone with access to a High Sierra Mac to take administrative control, Apple still has extra work to do to make its...
The group, called Google You Owe Us, said in a declaration Thursday that it was the first case of its sort in the U.K. against a major tech business over the alleged...
Amber is a proof of concept packer, it can pack regularly compiled PE files into reflective PE files that can be used as multi stage infection payloads. If you want to...
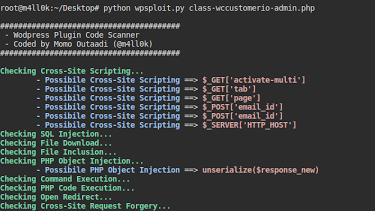
This tool is intended for Penetration Testers who audit WordPress plugins or developers who wish to audit their own WordPress plugins. For more info click here. Usage $...
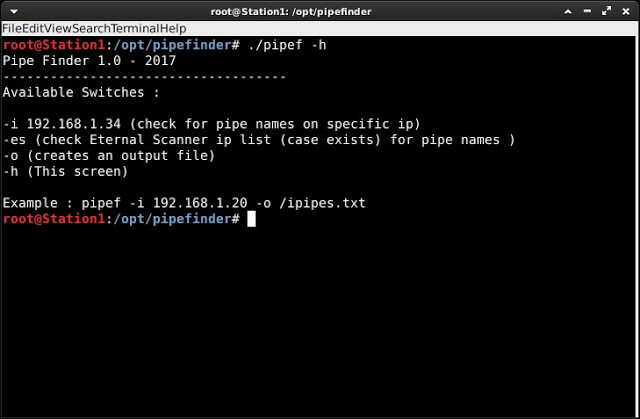
Automated script to search in SMB protocol for availables pipe names. Requirements metasploit-framework wget pipe_audit_v2.rb module () – It will be installed on...