Security researchers from FireEye and Dragos have discovered a nasty piece of malware targeting industrial control systems (ICS). The malware (called “TRITON” and...
A new plug-in called “Looking Glass” discovered in each instance of the new Firefox Quantum browser. It was turned off by default, but users were still scared to see a...
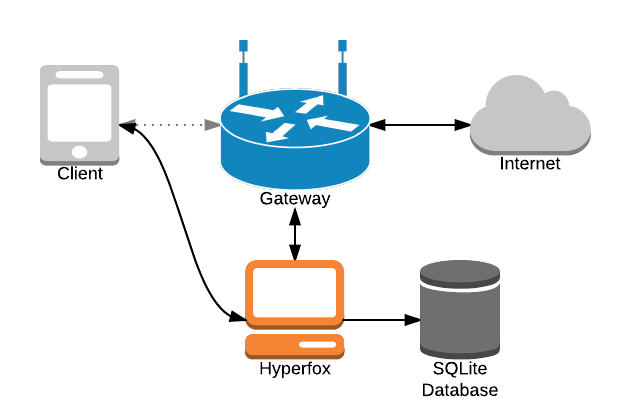
Hyperfox is a security tool for proxying and recording HTTP and HTTPs communications on a LAN. Hyperfox is capable of forging SSL certificates on the fly if you provide...
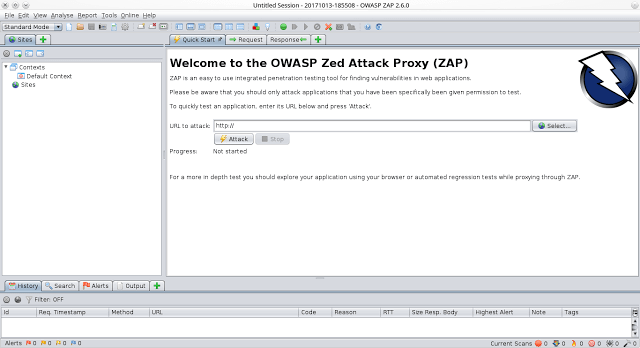
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It can help...
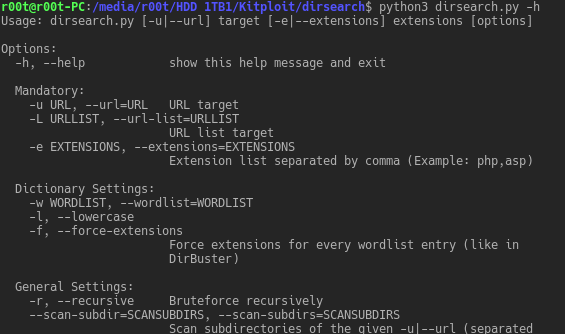
dirsearch is a simple command line tool designed to brute force directories and files in websites. Operating Systems supported Windows XP/7/8/10 GNU/Linux MacOSX...
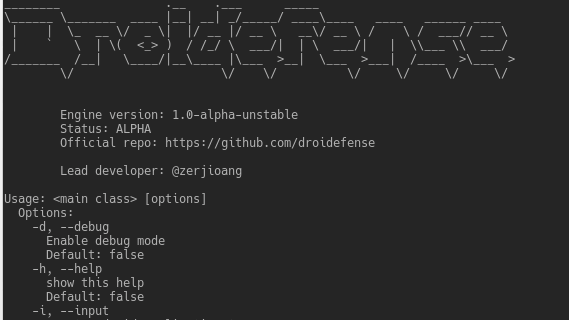
Droidefense (originally named atom: analysis through observation machine)* is the codename for android apps/malware analysis/reversing tool. It was built focused on...
The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over the air with...
Before you throw your computer into a lake, rest ensured this ain’t over. In the days, weeks, and periods to follow honestly, indeed in the next few hours the next phase...
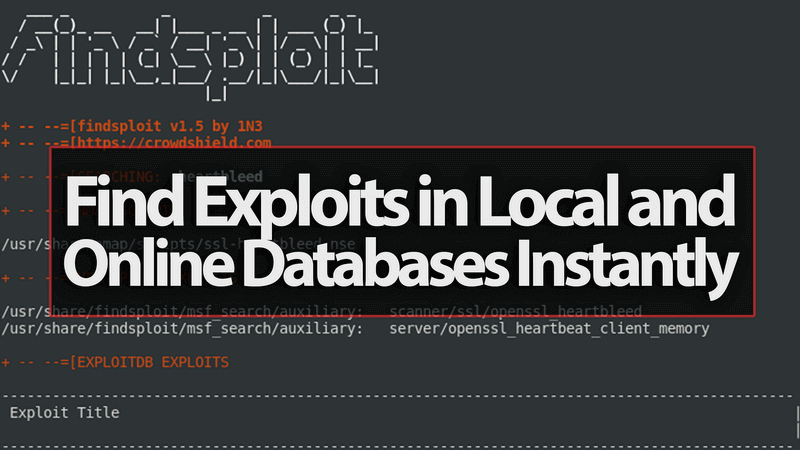
Findsploit is a simple bash script to quickly and easily search both local and online exploit databases. Findsploit: Installation: git clone cd Findsploit && ls...
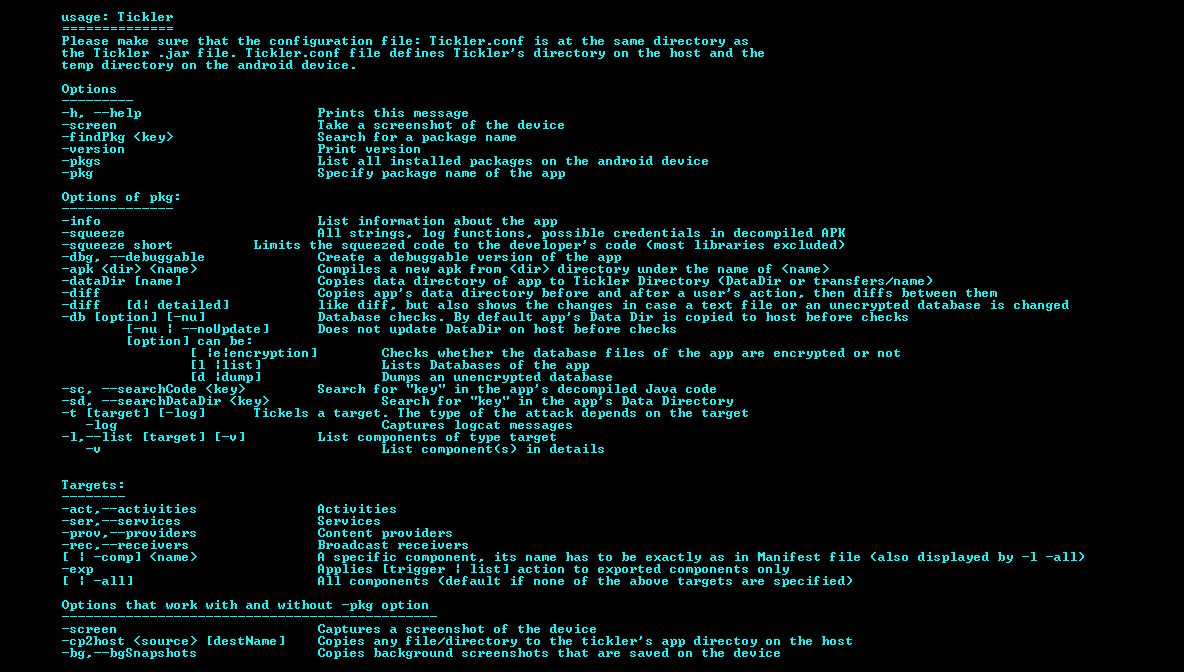
A java tool that helps to pentest Android apps faster, more easily and more efficiently. AndroTickler offers many features of information gathering, static and dynamic...