BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...
In a statement on Wednesday, the organization said slowing down the telephones via a recent software update was needed because the aging batteries in older phones were...
Youbit is a South Korean exchange that got hacked last week. As per reports, it is believed that around one-fifth of the clients’ holdings were stolen by unknown hackers...
Security researchers from security firm Elttam have discovered a critical vulnerability (tracked as CVE-2017-17562) in GoAhead tiny web server that affects many IoT...
Snowden told Moudeina that he was operating on an app that could turn a mobile device into a kind of motion sensor in form to notify you when your things are being...
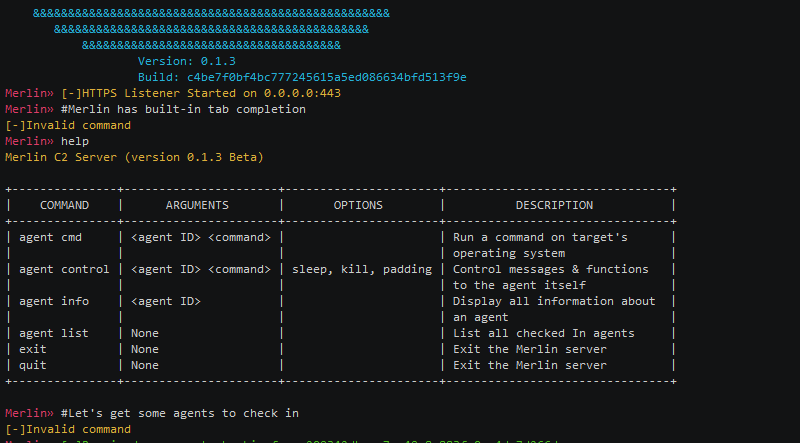
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that requests...
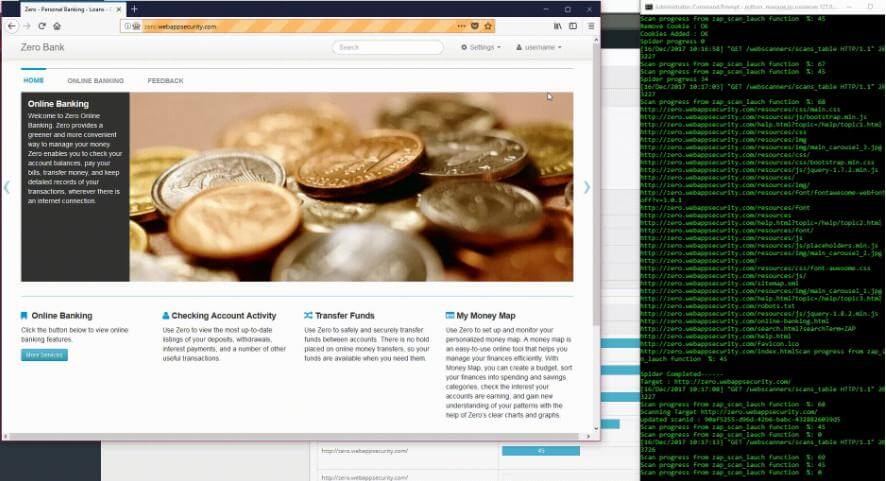
Archery is an opensource vulnerability assessment and management tool which helps developers and pentesters to perform scans and manage vulnerabilities. Archery uses...
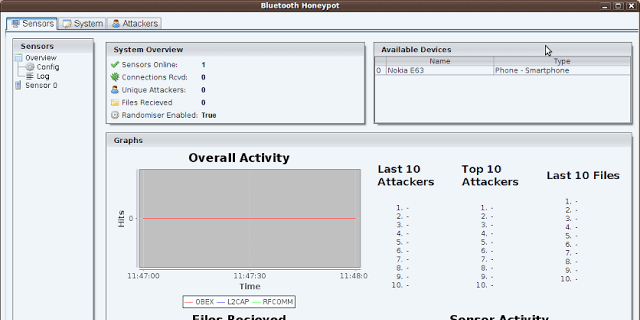
This code is from a University Project written in 2010. This is a newer version of the code than is on Google Code. Bluepot is a Bluetooth Honeypot written in Java, it...
The PowerUpSQL module includes functions that support SQL Server discovery, auditing for common weak configurations, and privilege escalation on scale. It is intended to...
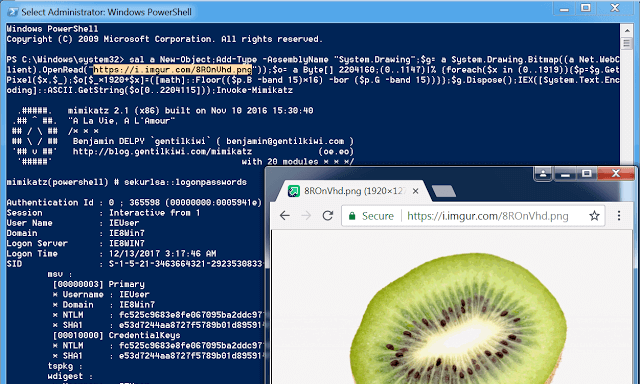
Invoke-PSImage takes a PowerShell script and embeds the bytes of the script into the pixels of a PNG image. It generates a oneliner for executing either from a file of...