shecoject is a tool written in python3, which can be used to package raw metasploit-generated raw files directly into the pyinstaller package or you can use this tool to...
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation Tools Sniffing...
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP Address Web...
This type of abusive conduct is possible because of a configuration flaw in the login handlers included with all browsers, login managers that allow browsers to memorize...
NTU researchers have revealed that smartphones can now be hacked using the data accumulated from sensors. Dr. Shivam, a scientist at NTU, who recently developed an app...
Fortify the security of any WordPress installation. This tool releases new versions on a regular basis. Make sure to update your dependencies frequently to get the...
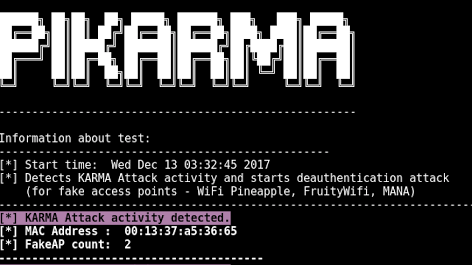
Detects wireless network attacks performed by KARMA module (fake AP). Starts deauthentication attack (for fake access points) Working Principle for PiKarma Collects all...
Zachary Buchta, a 20 year old hacker, who is the co-founder of famous hacking groups called Lizard Squad And Poodlecorp was recently in news for all the wrong reasons. A...
Russian ATMs Are Hackable It was recently revealed that some ATMs that are running in Russia are still operating on Windows XP operating system, which is why it is...
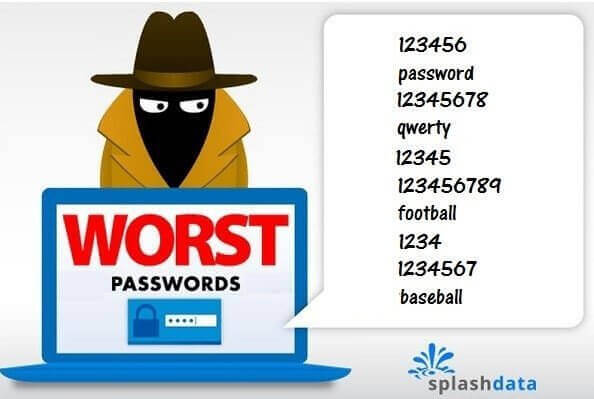
While becoming “123456” as your phrase is quite bad, the other phrases found on a list of Top 100 Worst Passwords of 2017 are just as distressing and remorseful. The...