[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
Category - Vulnerability Analysis
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure.
[sc name=”ad_1″] Create a vulnerable active directory that’s allowing you to test most of active directory attacks in local lab. Main...
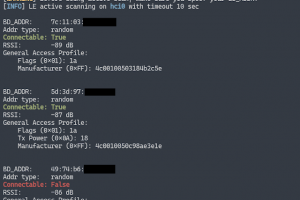
[sc name=”ad_1″] Bluescan is a open source project by Sourcell Xu from DBAPP Security HatLab. Anyone may redistribute copies of bluescan to anyone...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
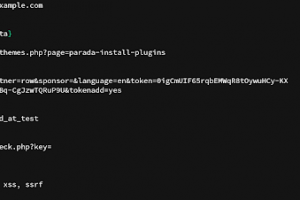
[sc name=”ad_1″] Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url=...
[sc name=”ad_1″] A new pentesting virtual environment for IoT Devices Download Link : MD5 : d9c20057b14cfa3fb25f744813b828df ; SHA1:...
[sc name=”ad_1″] A tool that detects the privilege escalation vulnerabilities caused by misconfigurations and missing updates in the Windows...
[sc name=”ad_1″] Oralyzer, a simple python script, capable of identifying the open redirection vulnerability in a website. It does that by fuzzing...
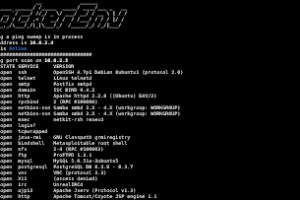
[sc name=”ad_1″] hackerEnv is an automation tool that quickly and easily sweep IPs and scan ports, vulnerabilities and exploit them. Then, it hands...
[sc name=”ad_1″] Tsunami is a general-purpose network security scanner with an extensible plugin system for detecting high severity vulnerabilities...