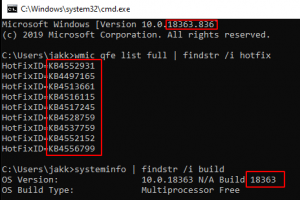
[sc name=”ad_1″] This is the code base for the service running on: . In short, PatchChecker is a web application (running on flask) that provides...
Category - Vulnerability Analysis
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure.
[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
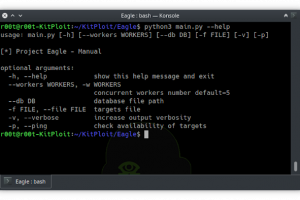
[sc name=”ad_1″] Project Eagle is a plugin based vulnerabilities scanner with threading support used for detection of low-hanging bugs on mass...
[sc name=”ad_1″] As indicated by sources like vulndb & cve, on a daily basis, approximately 50 new vulnerabilities become known to industry and...
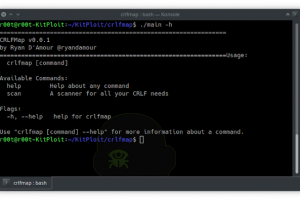
[sc name=”ad_1″] CRLFMap is a tool to find HTTP Splitting vulnerabilities Why? I wanted to write a tool in Golang for concurrency I wanted to be...
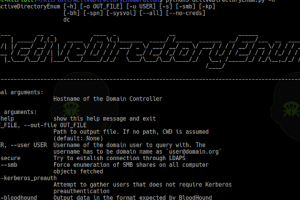
[sc name=”ad_1″] ADE – ActiveDirectoryEnum usage: activeDirectoryEnum [-h] [-o OUT_FILE] [-u USER] [-s] [-smb] [-kp] [-bh] [-spn] [--all] [...
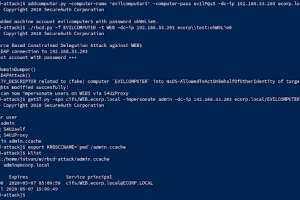
[sc name=”ad_1″] Abusing Kerberos Resource-Based Constrained Delegation TL;DR This repo is about a practical attack against Kerberos Resource-Based...
[sc name=”ad_1″] DockerENT is activE ruNtime application security scanning Tool (RAST tool) and framework which is pluggable and written in python...
[sc name=”ad_1″] Safety checks your installed dependencies for known security vulnerabilities. By default it uses the open Python vulnerability...
[sc name=”ad_1″] There are better ways than managing vulnerabilities with spreadsheets, especially when you are working with several tools. We know...