A Tool To Help You Manage Your Leaks Install sudo apt-get install mongodb-org screen pip3 install -r requeriments.txt Usage screen -S leakManager hug -f index...
Category - Vulnerability Analysis
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure.
Burp Suite extension is able to find reflected XSS on page in real-time while browsing on web-site and include some features as: Highlighting of reflection in...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...
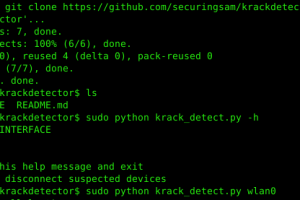
KRACK Detector is a Python script to detect possible KRACK attacks against client devices on your network. The script is meant to be run on the Access Point...
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on...
Blazy is a modern login page bruteforcer. Features Easy target selections Smart form and error detection CSRF and Clickjacking Scanner Cloudflare and WAF...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
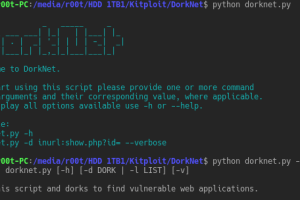
Selenium powered Python script to automate searching the web for vulnerable applications. DorkNet can take a single dork or a list of dorks as arguments. After...
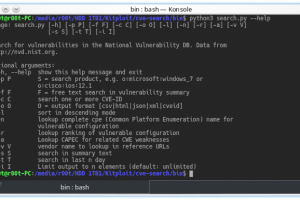
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
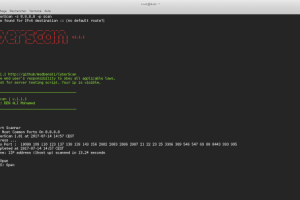
CyberScan is an open source penetration testing tool that can analyse packets , decoding , scanning ports, pinging and geolocation of an IP including...