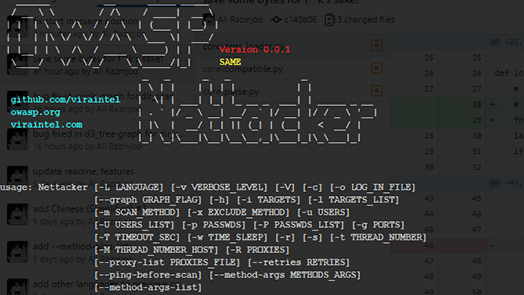
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
Category - Vulnerability Analysis
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure.
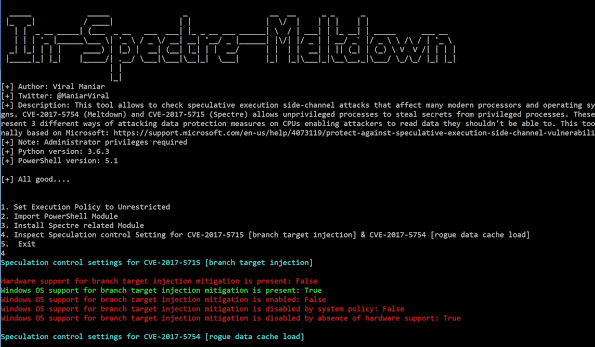
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown)...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
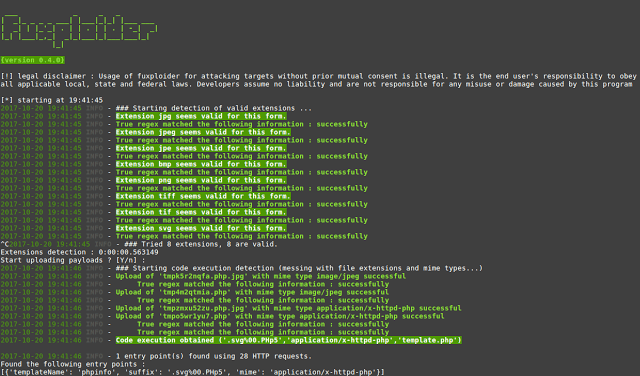
fuxploider is an open source penetration testing tool that automates the process of detecting and exploiting file upload forms flaws. This tool is able to...
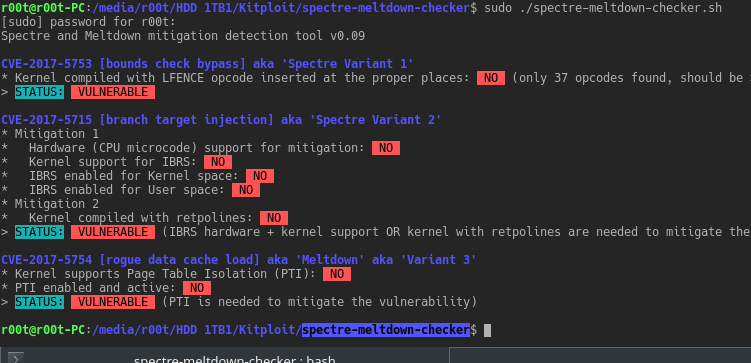
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
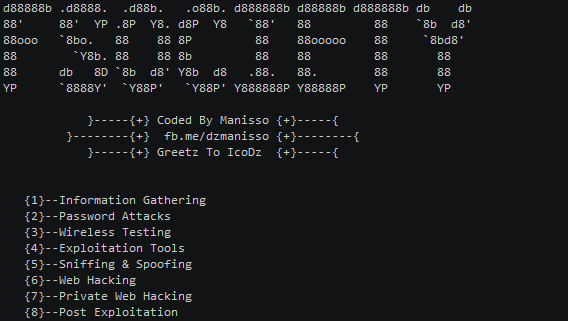
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
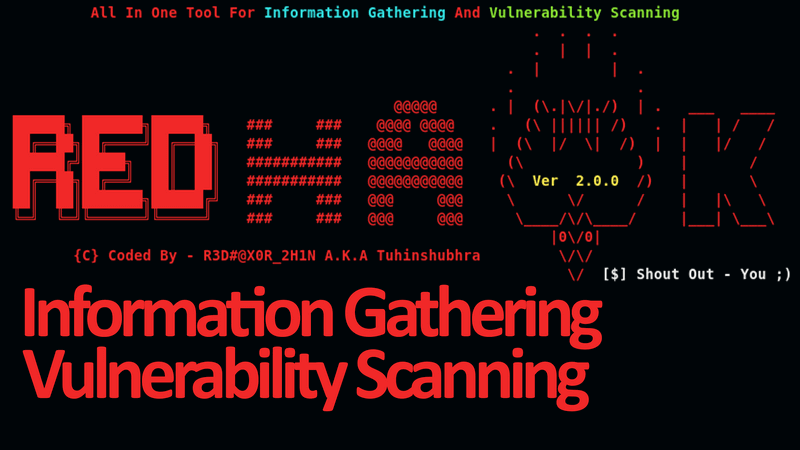
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
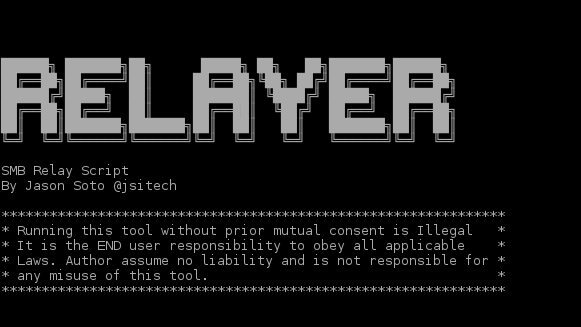
Relayer is an SMB relay Attack Script that automates all the necessary steps to scan for systems with SMB signing disabled and relaying authentication request...
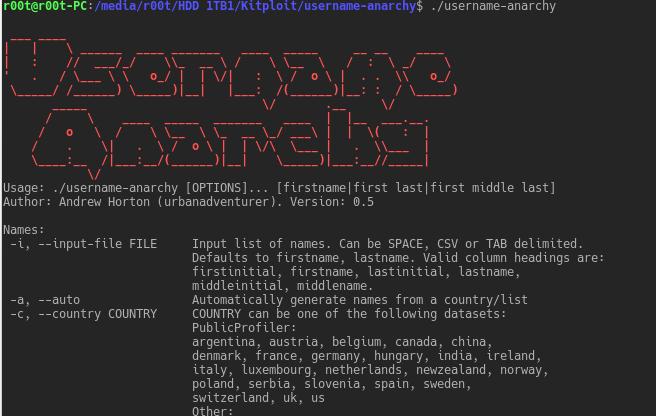
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...