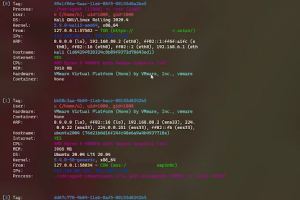
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
Category - Post Exploitation
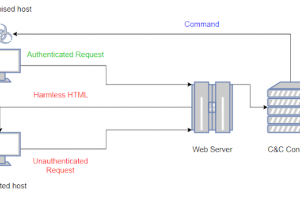
The purpose of the Post-Exploitation phase is to determine the value of the machine compromised and to maintain control of the machine for later use. The value of the machine is determined by the sensitivity of the data stored on it and the machines usefulness in further compromising the network.
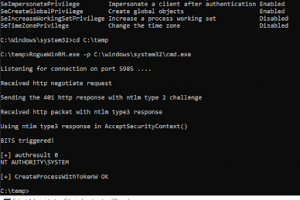
[sc name=”ad_1″] RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with SeImpersonatePrivilege) to...
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
[sc name=”ad_1″] A Cross Platform Remote Administration tool written in Go using Tor as its transport mechanism currently supporting Windows...
[sc name=”ad_1″] PYTMIPE (PYthon library for Token Manipulation and Impersonation for Privilege Escalation) is a Python 3 library for manipulating...
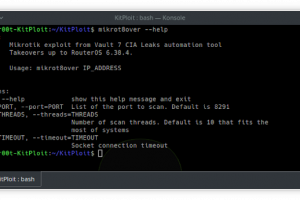
[sc name=”ad_1″] mikrot8over: Fast exploitation tool for Mikrotik RouterOS up to 6.38.4 This is reworked original Mikrotik Exploit. Added Python 2...
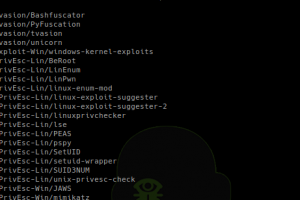
[sc name=”ad_1″] Some-Tools Why I was looking for a way to manage and keep up to date some tools that are not include in Kali-Linux. For exemple, I...
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
[sc name=”ad_1″] DeimosC2 is a post-exploitation Command & Control (C2) tool that leverages multiple communication methods in order to control...
[sc name=”ad_1″] This project still in BETA so you may face problems, Please open an issue so i’ll fix them..!! Hackingtool Menu AnonSurf...