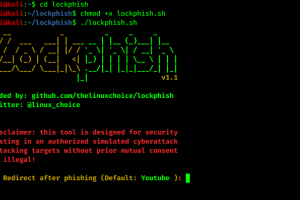
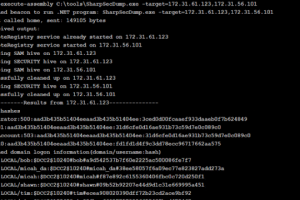
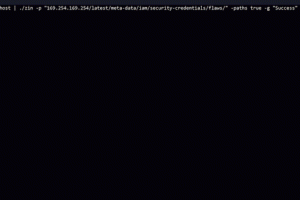
[sc name=”ad_1″] Lockphish it’s the first tool (07/04/2020) for phishing attacks on the lock screen, designed to grab Windows credentials...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
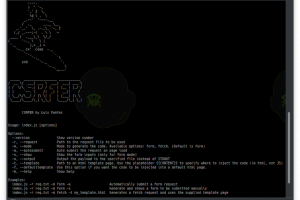
[sc name=”ad_1″] CSRFER is a tool to generate csrf payloads, based on vulnerable requests. It parses supplied requests to generate either a form or...
[sc name=”ad_1″] This Is Advance Phishing Tool! OTP PHISHING SPECIAL OTP BYPASS VIDEO WORKED Social Media Hack Link Installation Termux Whatsapp...
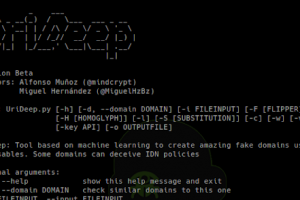
[sc name=”ad_1″] Unicode encoding attacks with machine learning. Tool based on machine learning to create amazing fake domains using confusables...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
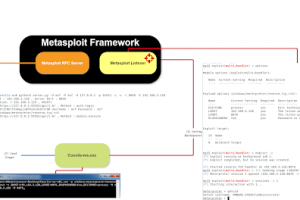
[sc name=”ad_1″] Cooolis-ms is a server that supports Metasploit Framework RPC. It is used to work for Shellcode and PE loader, bypassing the...
[sc name=”ad_1″] .Net port of the remote SAM + LSA Secrets dumping functionality of impacket’s secretsdump.py. By default runs in the context...
[sc name=”ad_1″] A Blind XSS Injector tool Features Inject Blind XSS payloads into custom headers Inject Blind XSS payloads into parameters...
[sc name=”ad_1″] A Payload Injector for bugbounties written in go Features Inject multiple payloads into all parameters Inject single payloads into...
[sc name=”ad_1″] Utility to find AES keys in running process memory. Works for 128, 192 and 256-bit keys. Usage Open aes-finder.sln solution in...