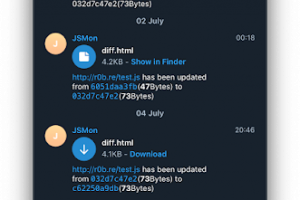
[sc name=”ad_1″] Using this script, you can configure a number of JavaScript files on websites that you want to monitor. Everytime you run this...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
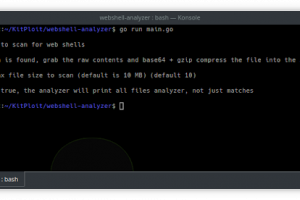
[sc name=”ad_1″] Web shell analyzer is a cross platform stand-alone binary built solely for the purpose of identifying, decoding, and tagging files...
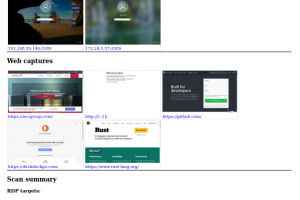
[sc name=”ad_1″] A new tool for collecting RDP, web and VNC screenshots all in one place This tool is still a work-in-progress and should be mostly...
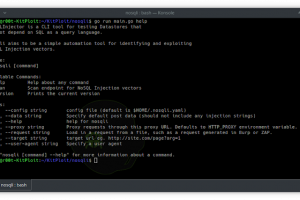
[sc name=”ad_1″] NoSQL scanner and injector. About Nosqli I wanted a better nosql injection tool that was simple to use, fully command line based...
[sc name=”ad_1″] GitDorker is a tool that utilizes the GitHub Search API and an extensive list of GitHub dorks that I’ve compiled from...
[sc name=”ad_1″] Malware Source Code Collection !!! DISCLAIMER !!! We do not take any responsibility for any damage done by the code in this...
[sc name=”ad_1″] The HUD is new interface that provides the functionality of ZAP directly in the browser. Learn more: Blog: Hacking with a Heads Up...
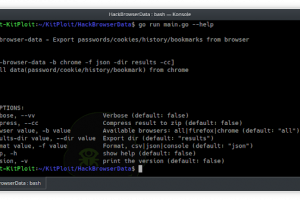
[sc name=”ad_1″] hack-browser-data is an open-source tool that could help you decrypt data (passwords / bookmarks / cookies / history) from the...
[sc name=”ad_1″] “MEDUZA” (“медуза”) means “jellyfish” in Ukrainian What is MEDUZA? It’s a Frida...
[sc name=”ad_1″] Gitjacker downloads git repositories and extracts their contents from sites where the .git directory has been mistakenly uploaded...