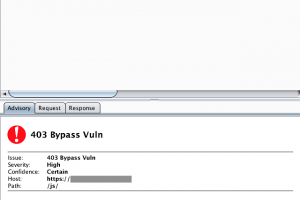
[sc name=”ad_1″] An burpsuite extension to bypass 403 restricted directory. By using PassiveScan (default enabled), each 403 request will be...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
[sc name=”ad_1″] A collection of proof-of-concept source code and scripts for executing remote commands over WinRM using the WSMan.Automation COM...
[sc name=”ad_1″] Features: Hacker Dashboard Hacker News [thehackernews.com/] New Exploits [Exploit-db.com] Hacking Tutorials Video [youtube.com]...
[sc name=”ad_1″] Multi-threaded c2 server and reverse TCP shell client written in pure C (Windows). Command list: list: list available connections...
[sc name=”ad_1″] This is a proof of concept of how a ransomware works, and some techniques that we usually use to hijack our files. This project is...
[sc name=”ad_1″] Karkinos is a light-weight ‘Swiss Army Knife’ for penetration testing and/or hacking CTF’s. Currently, Karkinos...
[sc name=”ad_1″] Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a...
[sc name=”ad_1″] Damn Vulnerable Bank Android Application aims to provide an interface for everyone to get a detailed understanding with internals...
[sc name=”ad_1″] N1QLMap is an N1QL exploitation tool. Currently works with Couchbase database. The tool supports data extraction and performing...
[sc name=”ad_1″] An organizational asset and vulnerability management tool, with Jira integration, designed for generating application security...