Apple’s privacy signs do not spread to the thousands of app developers who will gain access to facial data in order to increase entertainment features for...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...
In 2013, Hackers apparently gained access to the Trump Organization’s domain booking account and created at least 250 website subdomains that cybersecurity...
The CryptoShuffler malware has been discovered by security researchers from Kaspersky Lab, cybercriminals are using this malware to steal cryptocurrencies from...
The cryptocurrency has had a bullish streak completely the week following the CME’s statement that it will introduce bitcoin expectations contracts. According...
As we’ve seen, that’s been shifting. With a new game from companies like Hulu and Amazon, Netflix has seen running deals get pricier and customers get antsier...
Critically, both OS updates address the KRACK Wi-Fi vulnerability for any devices. It is a dangerous vulnerability in the WPA2 Wi-Fi assurance standard that...
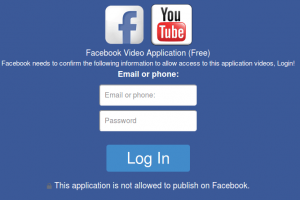
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
SpaceX has begun, on average, about 1.5 times per period during this year. From that view, the company’s 16th launch of 2017 may not appear all that...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...