In the past few periods, we’ve seen an escalation in the volatility in the state of Bitcoin and a notable increase in the fees to process activities on the...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
The researchers demanded data left visible entered names, phone numbers, locations and Google queries. The chief of the Israeli company back the app confirmed...
It’s the latest movement in a clash between Amazon and Google, which has seen the two businesses hold their products off the rival’s programs and services...
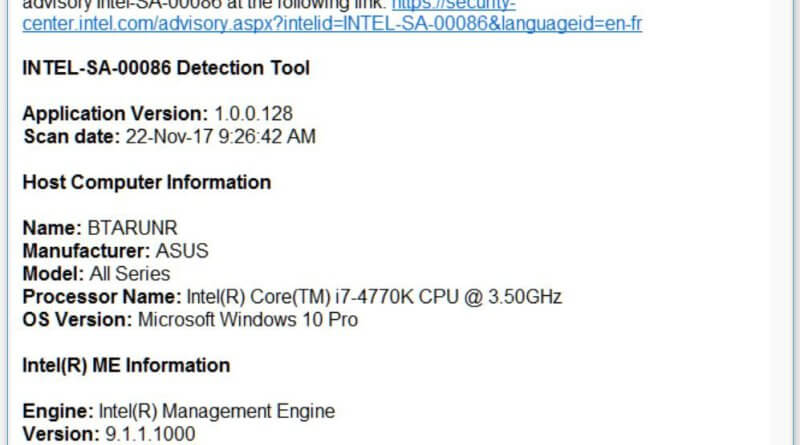
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later...
After rapidly reinforcing a flaw that acknowledged anyone with access to a High Sierra Mac to take administrative control, Apple still has extra work to do to...
The group, called Google You Owe Us, said in a declaration Thursday that it was the first case of its sort in the U.K. against a major tech business over the...
Google has explicitly rejected them from the Play Store. Identify Airpush? The current advertisement scourge is ad-infused lock screens, which have shown up in...
The cryptocurrency fell as greatly as 8 percent on Thursday on the Luxembourg confirmed Bitstamp exchange to hit $9,000 exactly, considering a fall of well...
The term “location services” oftentimes points to exact GPS data for app usage, such as Google Maps discovering your best commute route, or Uber figuring...