Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
Palihapitiya’s judgments were directed not only at Facebook but the broader online ecosystem. “The short-term, dopamine-driven feedback circles we’ve produced...
On December 14, the company will vote to repeal the net neutrality practices it put in place in 2015. With Republicans agents who oppose the rules outnumbering...
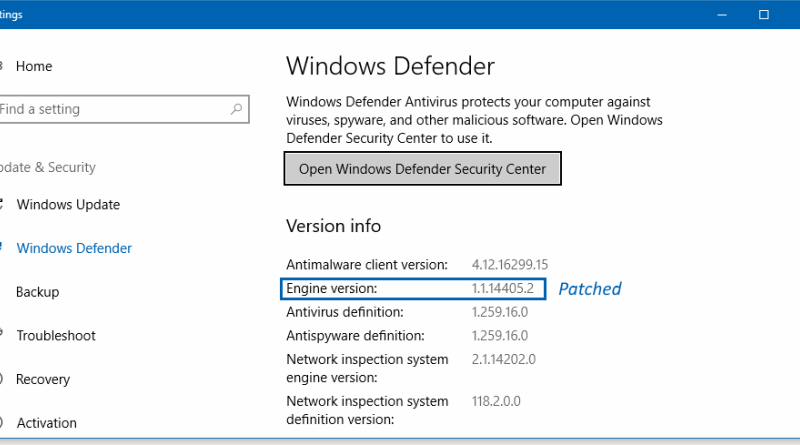
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...
Denis Sinegubko (a security researcher from Sucuri) has discovered a new wave of the known malware wp-vcd that injects malicious WordPress admin users into...
The keylogging code was embedded in the SynTP.sys file, which is a module of the Synaptics Touchpad driver that ships with HP notebook models. “The logging was...
The Partnership sounds like something that would result on Facebook or Twitter, which are rife with imprinted content not on a site like Reddit. Well...
The flaw has been discovered by security researchers from the University of Birmingham, who tested hundreds of various banking applications and discovered that...
Bitcoin is breaking every record—after gaining 20% jump last week, Bitcoin price just crossed the $14,800 mark in less than 24 hours—and there can be no better...