This type of abusive conduct is possible because of a configuration flaw in the login handlers included with all browsers, login managers that allow browsers...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
NTU researchers have revealed that smartphones can now be hacked using the data accumulated from sensors. Dr. Shivam, a scientist at NTU, who recently...
Zachary Buchta, a 20 year old hacker, who is the co-founder of famous hacking groups called Lizard Squad And Poodlecorp was recently in news for all the wrong...
Russian ATMs Are Hackable It was recently revealed that some ATMs that are running in Russia are still operating on Windows XP operating system, which is why...
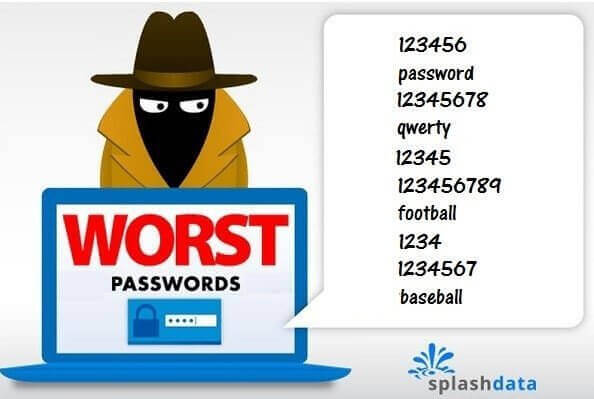
While becoming “123456” as your phrase is quite bad, the other phrases found on a list of Top 100 Worst Passwords of 2017 are just as distressing and...
The administration of Guangzhou, center of the southern coastal province of Guangdong, began on Monday a pilot plan that creates a virtual ID card, which...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...
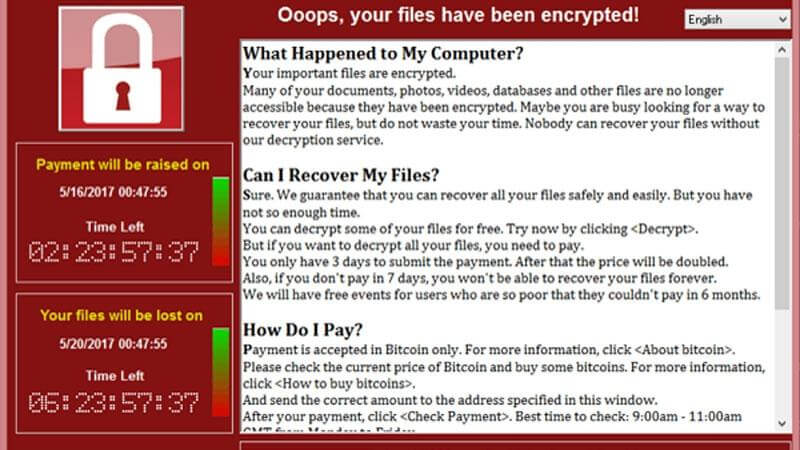
North Korea says there is no evidence to back the US claim it was behind the WannaCry ransomware attack. The US was “unreasonably accusing the DPRK...
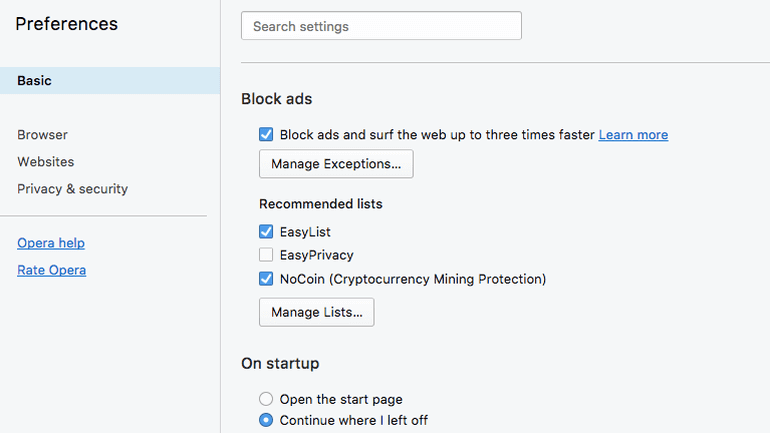
Norwegian browser maker Opera has launched the beta version of Opera 50, the first popular browser to integrate a built-in cryptocurrency-mining blocker. The...
In a statement on Wednesday, the organization said slowing down the telephones via a recent software update was needed because the aging batteries in older...