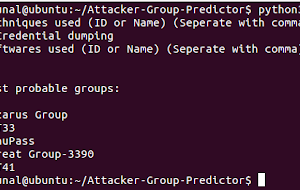
[sc name=”ad_1″] The tool predicts attacker groups from techniques and softwares used. It searches based on the MITRE ATT&CK framework How it...
Author - Mazen Elzanaty
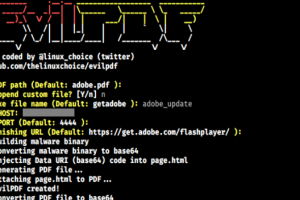
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Hiding executable files in PDF documents Legal disclaimer: Usage of...
[sc name=”ad_1″] Chrome extension for Instant access to your bug bounty submission dashboard of various platforms + publicly disclosed reports +...
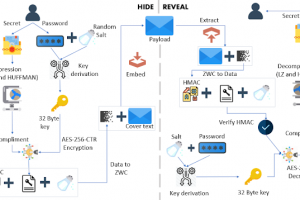
[sc name=”ad_1″] StegCloak is a pure JavaScript steganography module designed in functional programming style, to hide secrets inside text by...
[sc name=”ad_1″] RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without...
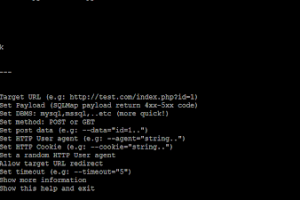
[sc name=”ad_1″] Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code...
[sc name=”ad_1″] This is a basic C2 generic server written in Python and Flask. This code has based ideia to GTRS, which uses Google Translator as...
[sc name=”ad_1″] URLCrazy is an OSINT tool to generate and test domain typos or variations to detect or perform typo squatting, URL hijacking...
[sc name=”ad_1″] Impost3r is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C. Attackers can use Impost3r...
[sc name=”ad_1″] Zoom Conference scanner. This scanner will check for a random meeting id and return information if available. Usage This are all...