[sc name=”ad_1″]
The tool predicts attacker groups from techniques and softwares used. It searches based on the MITRE ATT&CK framework
How it works?
- 1- Collect data from https://attack.mitre.org/ about attacker groups
- 2- Get data from user about attack
- 3- Compare data and create result
Installation
git clone https://github.com/omergunal/Attacker-Group-Predictor.git
cd Attacker-Group-Predictor/
pip3 install -r requirements.txtUsage
python3 main.py
Fill the inputsUpdate Attacker Groups Data
cd updater
python3 update.pyExample
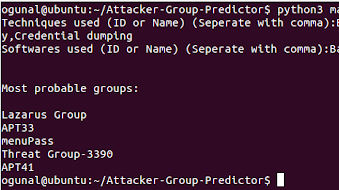
python3 main.py
Techniques used (ID or Name) (Seperate with comma):Brute Force,Commonly used port,connection proxy,Credential dumping
Softwares used (ID or Name) (Seperate with comma):Bankshot,mimikatz,RawdiskMost probable groups:
Lazarus Group
APT33
menuPass
Threat Group-3390
APT41
[sc name=”ad-in-article”]


















Add Comment