[sc name=”ad_1″] Bug Bounty Recon (bbrecon) is a free Recon-as-a-Service for bug bounty hunters and security researchers. The API aims to provide a...
Author - Mazen Elzanaty
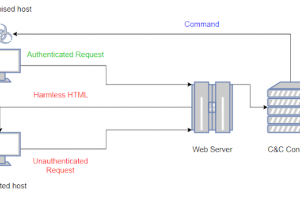
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
[sc name=”ad_1″] SpaceSiren is a honey token manager and alert system for AWS. With this fully serverless application, you can create and manage...
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
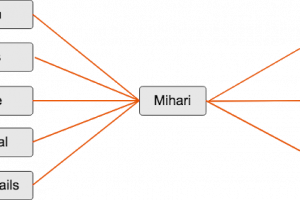
[sc name=”ad_1″] Mihari is a helper to run queries & manage results continuously. Mihari can be used for C2, landing page and phishing hunting...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
[sc name=”ad_1″] A golang utility to spider through a website searching for additional links with support for JavaScript rendering. Install go get ...