Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon – HackSmith v1.0.
Capabilities
- Scan a network (a particular subnet or a list of IP addresses) for all IP addresses associated with active network devices
- Determine the type of devices using fingerprinting
- Determine if there are any open ports on the device
- Associate the ports with common services
- Test devices against a dictionary of factory default and common credentials
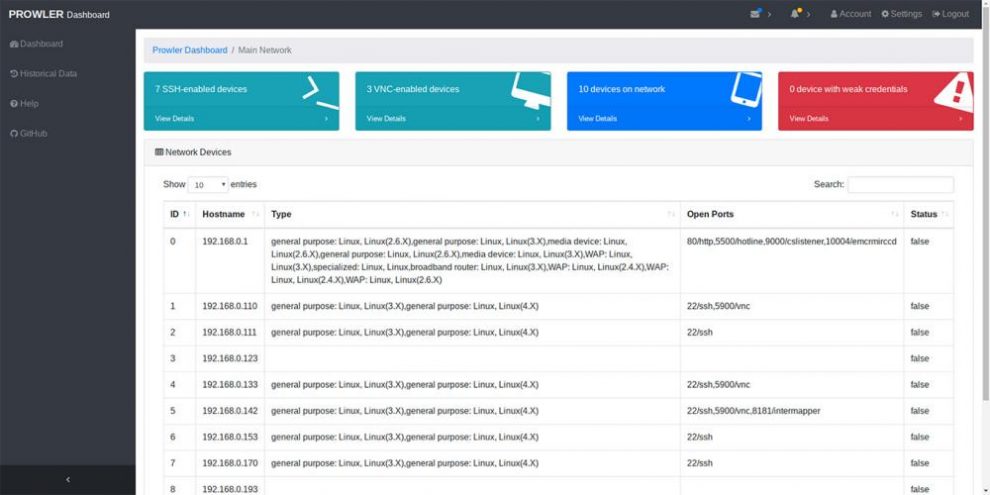
- Notify users of security vulnerabilities through an dashboard. Dashboard tour
Planned Capabilities
- Greater variety of vulnerability assessment capabilities (webapp etc.)
- Select wordlist based on fingerprint
Hardware
- Raspberry Pi Cluster HAT (with 4 * Pi Zero W)
- Raspberry Pi 3
- Networking device

Raspberry Pi 3 Model B+ is now on sale for $35
Software Stack
- Raspbian Stretch (Controller Pi)
- Raspbian Stretch Lite (Worker Pi Zero)
- Note: For ease of setup, use the images provided by Cluster Hat! Instructions
- Python 3 (not tested on Python 2)
- Python packages see
requirements.txt - Ansible for managing the cluster as a whole (
/playbooks)
Key Python Packages:
dispy(website) is the star of the show. It allows allows us to create a job queue that will be processed by the worker nodes.python-libnmapis the python wrapper around nmap, an open source network scanner. It allows us to scan for open ports on devices.paramikois a python wrapper around SSH. We use it to probe SSH on devices to test for common credentials.eelis used for the web dashboard (seperate repository, here)rabbitmq(website) is used to pass the results from the cluster to theeelserver that is serving the dashboard page.
Deploying Prowler
- Clone the git repository:
git clone https://github.com/tlkh/prowler.git - Install dependencies by running
sudo pip3 install -r requirements.txton the controller Pi - Run
ansible-playbook playbooks/setup_node.ymlto install the required packages on worker nodes. - Clone the prowler and dispy repositories to the worker nodes using
ansible-playbook playbooks/clone_repos.yml - Run
clusterhat onon the controller Pi to ensure that all Pi Zeros are powered up. - Run
python3 cluster.pyon the controller Pi to start Prowler
To edit the range of IP addresses being scanned, edit the following lines in cluster.py:
test_range = []
for i in range(0, 1):
for j in range(100, 200):
test_range.append("172.22." + str(i) + "." + str(j))



















Add Comment