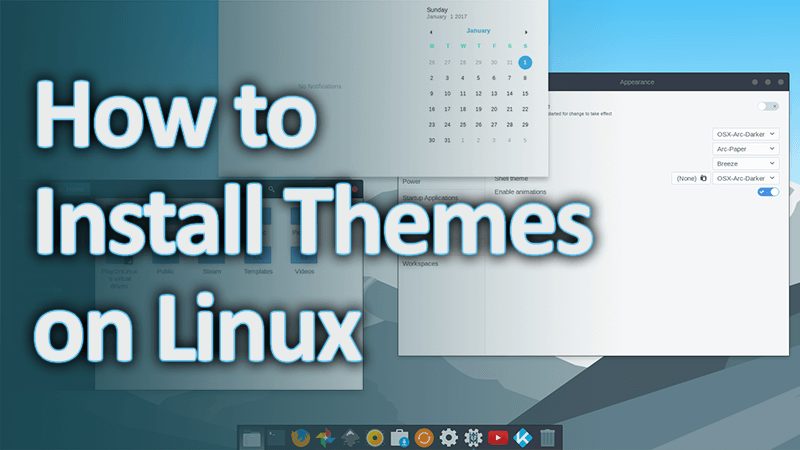
[sc name=”ad_1″] A theme is a collection of background image, window color and with theme can be given according to the picture as you wish. images...
Archive - July 2018
In computing, load balancing improves the distribution of workloads across multiple computing resources, such as computers, a computer cluster, network links...
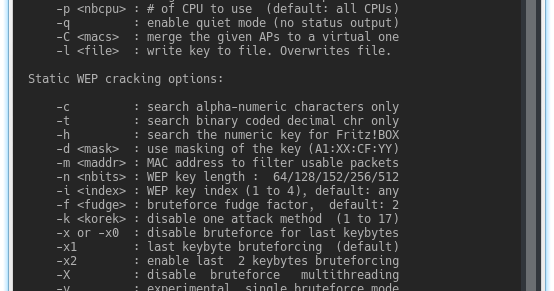
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
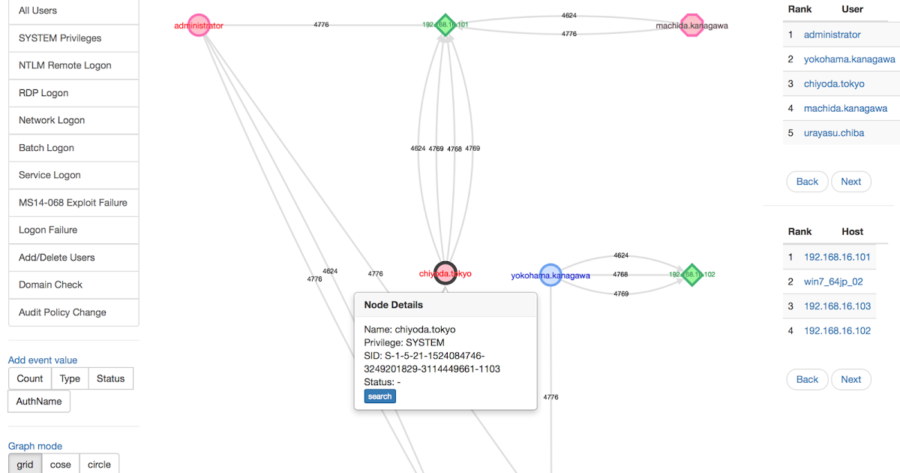
Investigate malicious logon by visualizing and analyzing Windows active directory event logs. Concept LogonTracer associates a host name (or an IP address) and...
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...
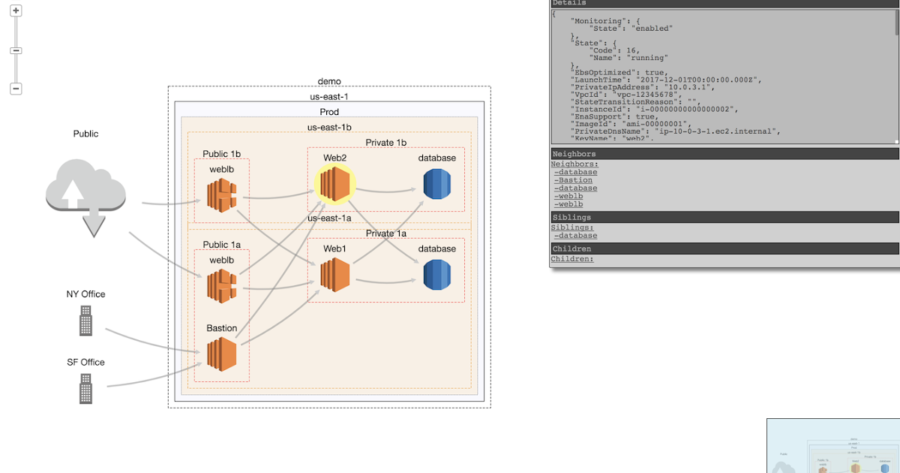
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...
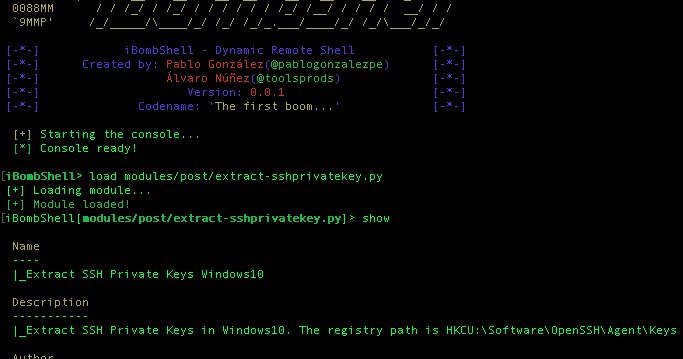
ibombshell is a tool written in Powershell that allows you to have a prompt at any time with post-exploitation functionalities (and in some cases exploitation)...
A Penetration Testing Framework created for Hackers / Pentester / Bug Hunter Menu Web Pentest | Banner Grab | Whois | Traceroute | DNS Record | Reverse DNS...
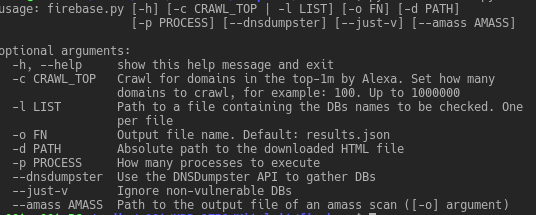
Exploiting vulnerable/misconfigured Firebase databases Prerequisites Non-standard python modules: dnsdumpster bs4 requests Installation If the following...
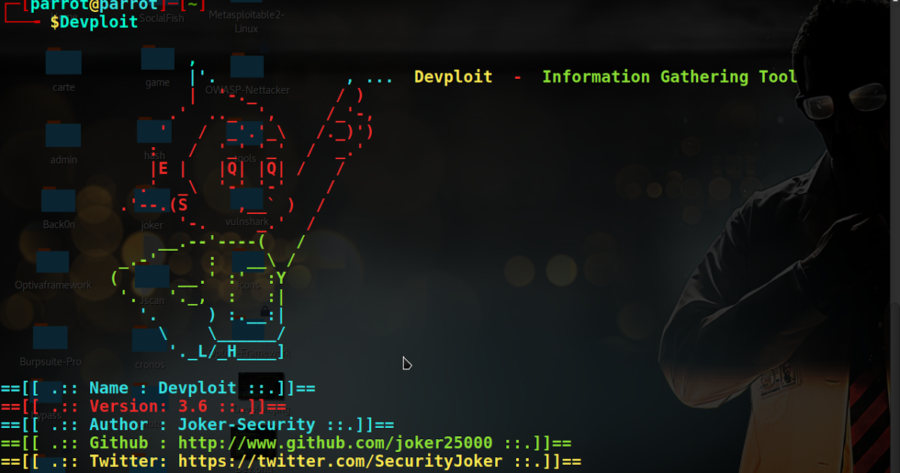
Devploit is a simple python script to Information Gathering. Download: git clone How to use: cd Devploit chmod +x install ./install Run in Terminal Devploit...