Tor enables users to surf the Internet, chat and send instant messages anonymously, and is used by a wide variety of people for both Licit and Illicit purposes...
Archive - June 2018
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
Pwnie Island is a limited-release, first-person, true open-world MMORPG set on a beautiful island where anything could happen. That’s because this game...
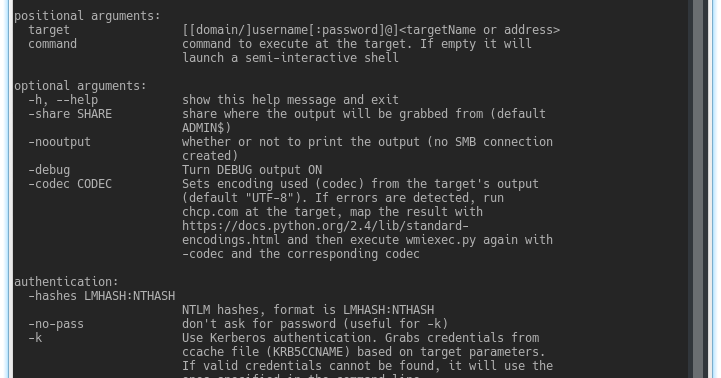
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
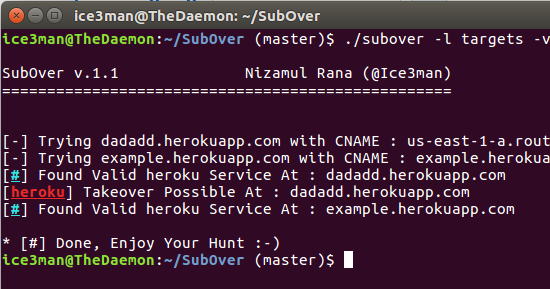
[sc name=”ad_1″] Subover is a Hostile Subdomain Takeover tool originally written in python but rewritten from scratch in Golang. Since it’s...
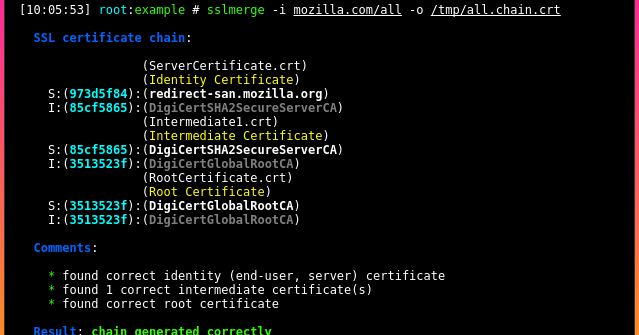
Is an open source tool to help you build a valid SSL certificate chain from the root certificate to the end-user certificate. Also can help you fix the...
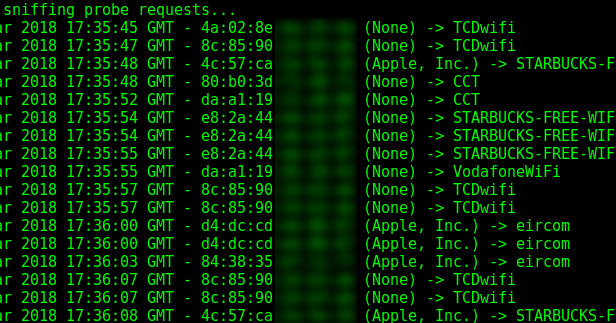
Toolkit allowing to sniff and display the Wi-Fi probe requests passing near your wireless interface. Probe requests are sent by a station to elicit information...
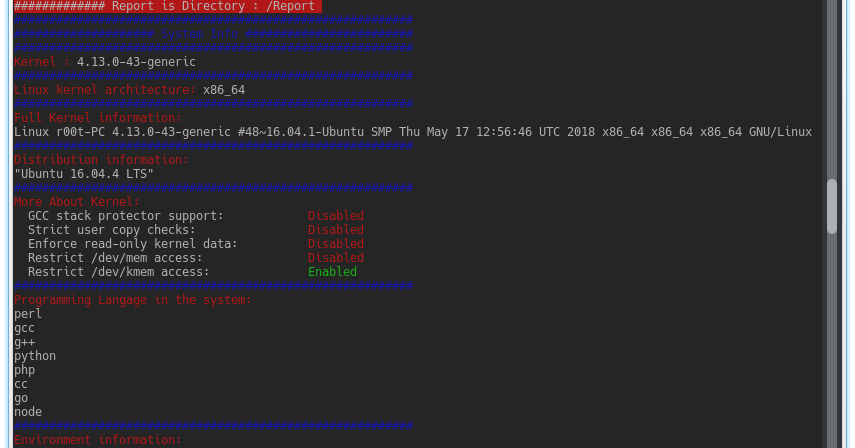
New Linux Privilege Escalation Tool. Getting Started System Information Gatherer Kernel Information Gatherer Checking Development environments on the system...
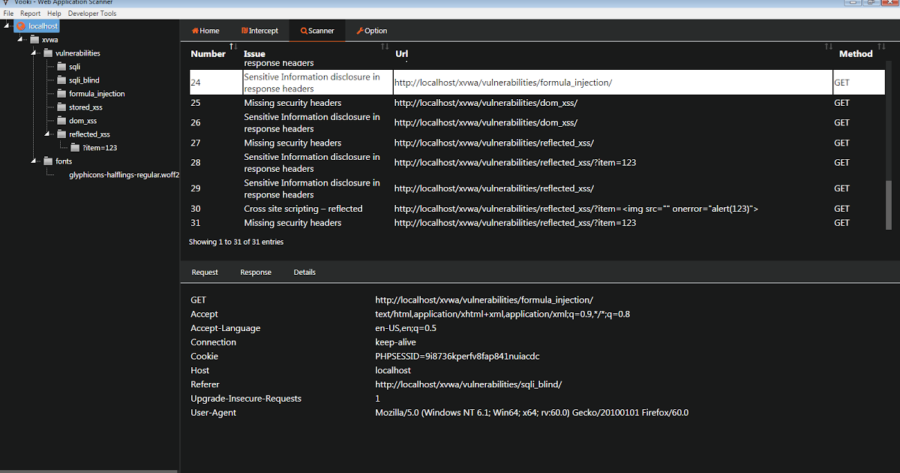
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities...
Gpredict is a real time satellite tracking and orbit prediction program for the Linux desktop. It uses the SGP4/SDP4 propagation algorithms together with NORAD...