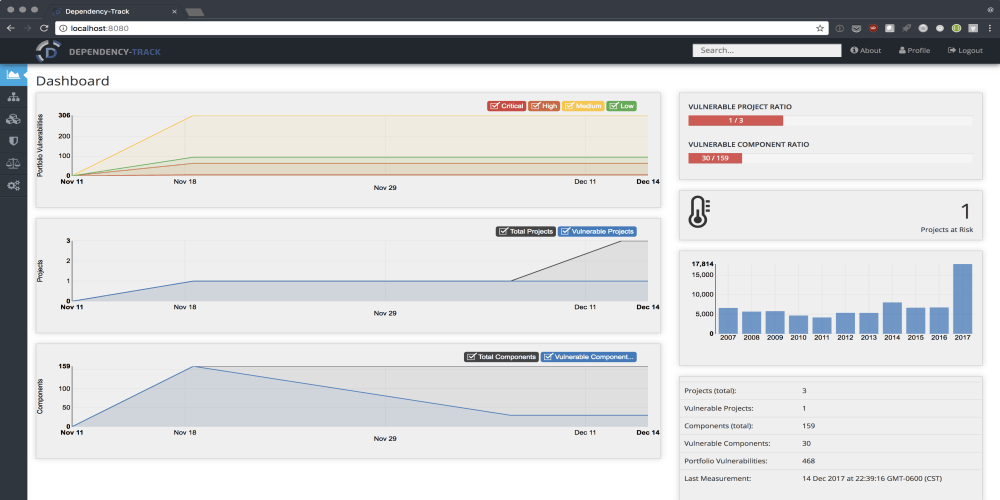
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
Archive - February 2018
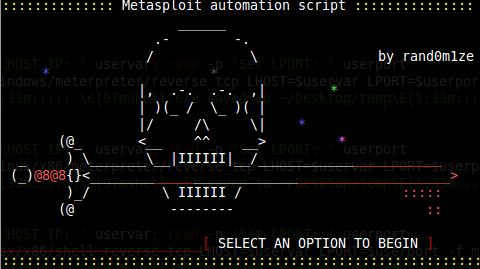
Command line script for automating metasploit functions: Checks for metasploit service and starts if not present Easily craft meterpreter reverse_tcp...
Script to steal passwords from SSH. Install git clone cd sshLooter Configuration Edit the script on install.sh, and add your telegram bot api, and your userid...
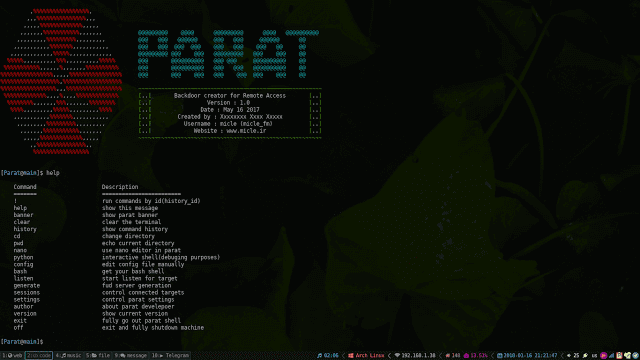
Parat is a simple remote administration tool (RAT) written in python. Also you can read wiki! Change log: Compatible with both python 2 and 3 versions(dont...
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of...
[sc name=”ad_1″] Hacking a Wi-Fi network using Kali Linux needs a wireless card that support monitor mode and packet injection. Not all wireless...
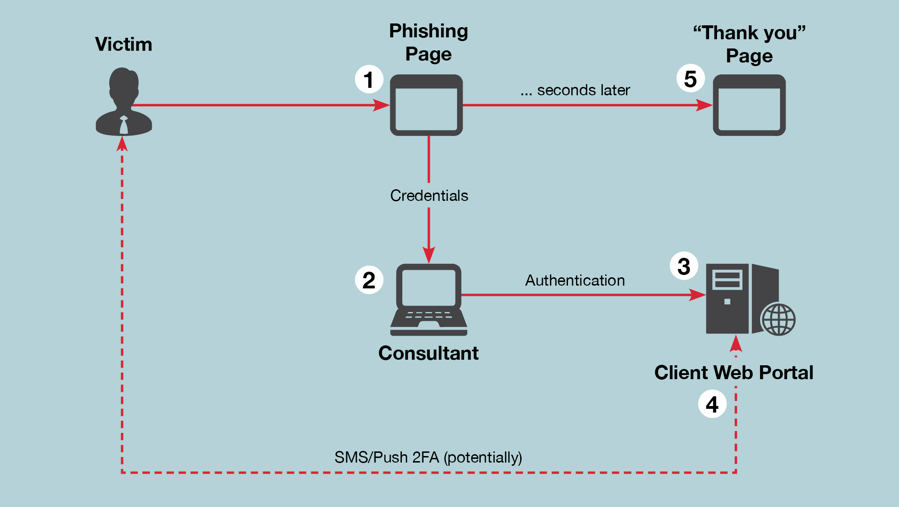
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
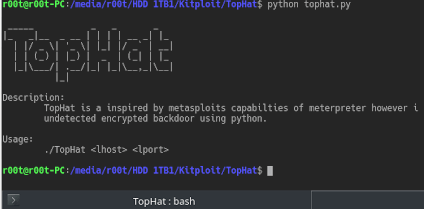
TopHat is a inspired by metasploits capabilties of meterpreter however i have coded a script to generate a undetected encrypted backdoor using python. Usage:...
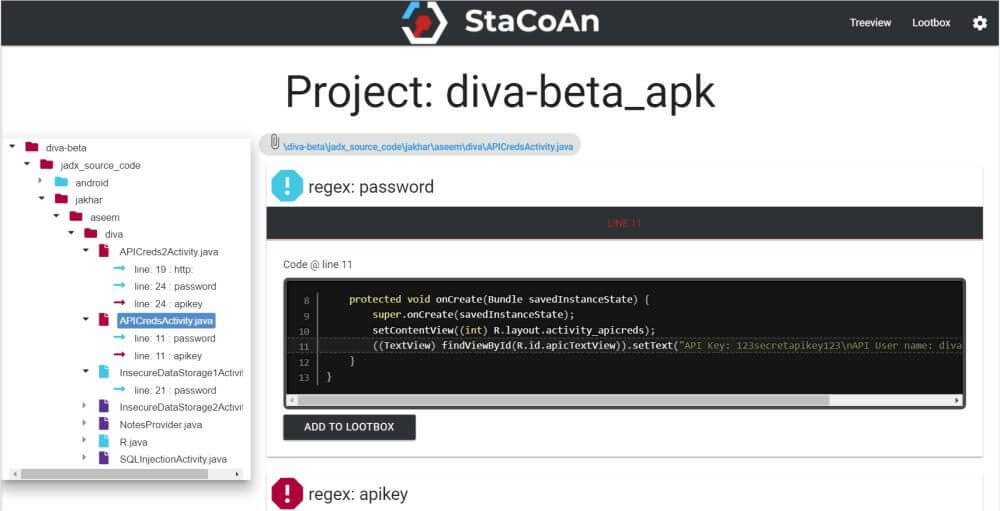
StaCoAn is a crossplatform tool which aids developers, bugbounty hunters and ethical hackers performing static code analysis on mobile applications. This tool...
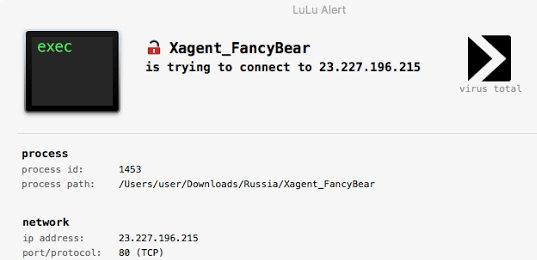
LuLu is the free open-source macOS firewall that aims to block unauthorized (outgoing) network traffic, unless explicitly approved by the user: Full details...