Collaborative (mitm) cryptocurrency mining pool in wifi networks. This script performs autonomous MITM attack on WiFi networks. It will inject a javascript in...
Archive - January 2018
DNSExfiltrator allows for transfering (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate...
SDRtrunk is an integrated application for demodulating radio signals and decoding trunked radio network protocols and some related radio signal formats. The...
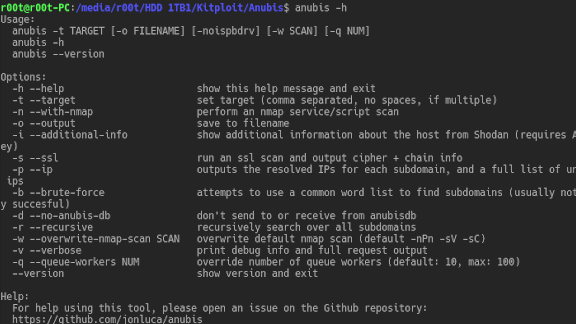
Anubis is a subdomain enumeration and information gathering tool. Anubis collates data from a variety of sources, including HackerTarget, DNSDumpster, x509...
Microsoft is addressing unusual of the performance subdividing for fixing patches to relieve the Meltdown and Spectre vulnerabilities. Windows Chief Terry...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
At last, Wi-Fi security — or lack of — is about to get its day in the sun. The Wi-Fi Alliance, an industry body made up of device makers including...
Millions of people have become victims of a FakeApp that is using new tricks to cheat Uber users around the world. Security researchers from Symantec...
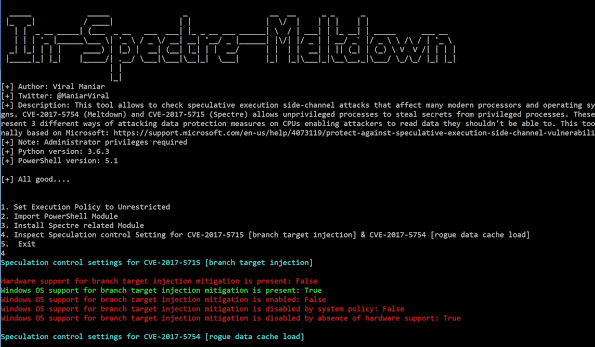
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown)...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...