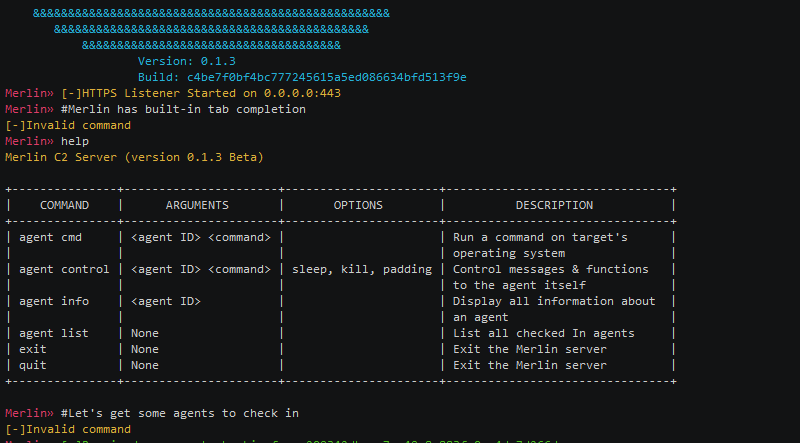
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
Archive - December 2017
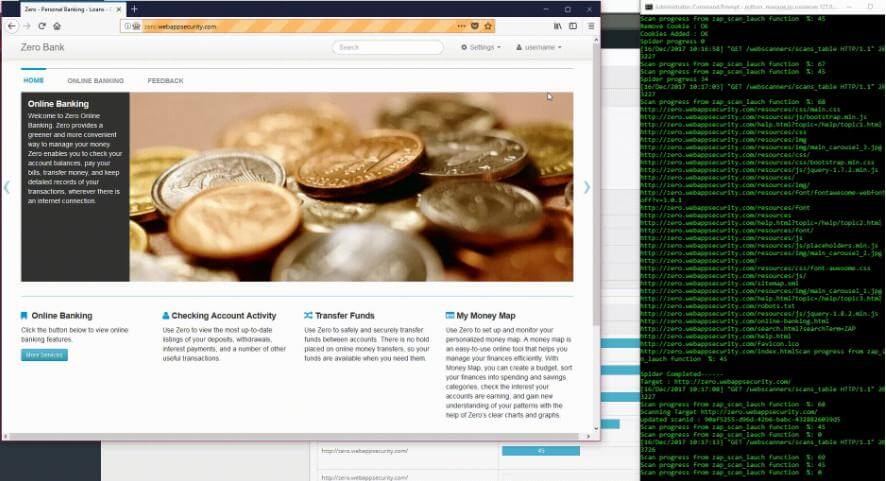
Archery is an opensource vulnerability assessment and management tool which helps developers and pentesters to perform scans and manage vulnerabilities...
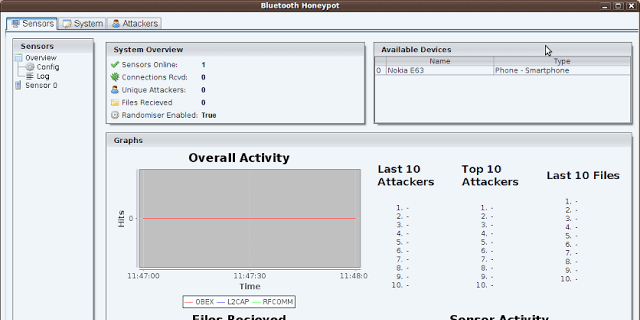
This code is from a University Project written in 2010. This is a newer version of the code than is on Google Code. Bluepot is a Bluetooth Honeypot written in...
The PowerUpSQL module includes functions that support SQL Server discovery, auditing for common weak configurations, and privilege escalation on scale. It is...
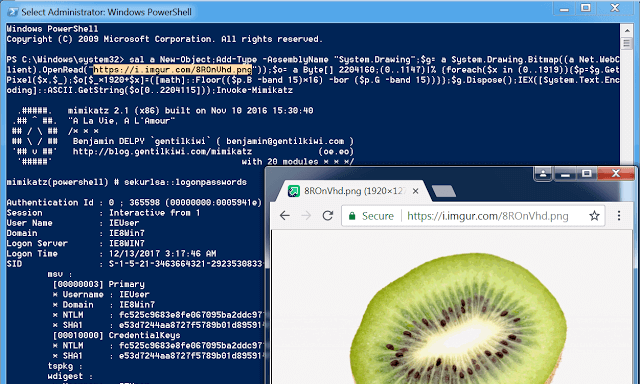
Invoke-PSImage takes a PowerShell script and embeds the bytes of the script into the pixels of a PNG image. It generates a oneliner for executing either from a...
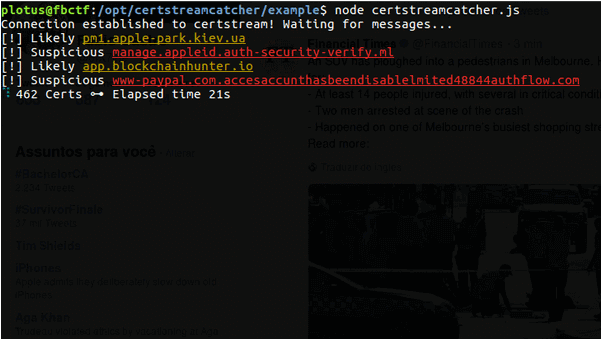
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
A script for installing and automatically configuring DNSCrypt on Linux-based systems. Description DNSCrypt is a protocol for securing communications between a...
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
The corporation says that version 390 of its GPU video driver will be the last to carry 32-bit platforms. “Later driver release reports will not operate, nor...
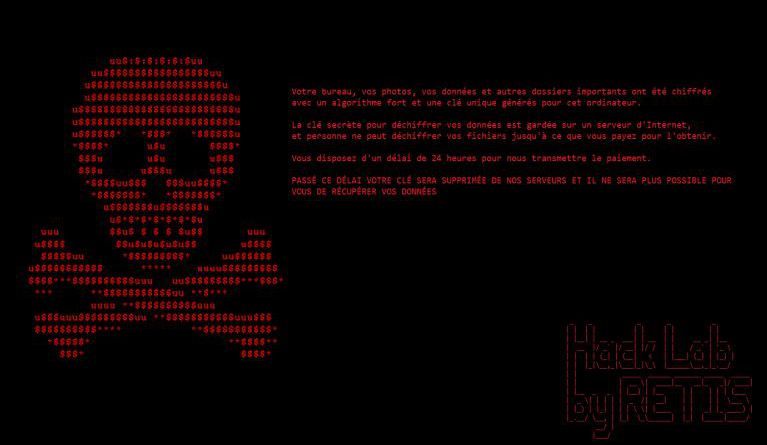
A security researcher has discovered a ransomware called Retis, which is a ransomware-type virus that secretly infiltrates the system. Shortly after executed...