Fortify the security of any WordPress installation. This tool releases new versions on a regular basis. Make sure to update your dependencies frequently to...
Archive - December 2017
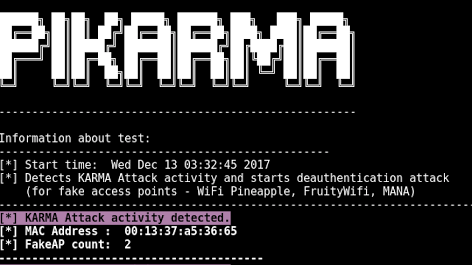
Detects wireless network attacks performed by KARMA module (fake AP). Starts deauthentication attack (for fake access points) Working Principle for PiKarma...
Zachary Buchta, a 20 year old hacker, who is the co-founder of famous hacking groups called Lizard Squad And Poodlecorp was recently in news for all the wrong...
Russian ATMs Are Hackable It was recently revealed that some ATMs that are running in Russia are still operating on Windows XP operating system, which is why...
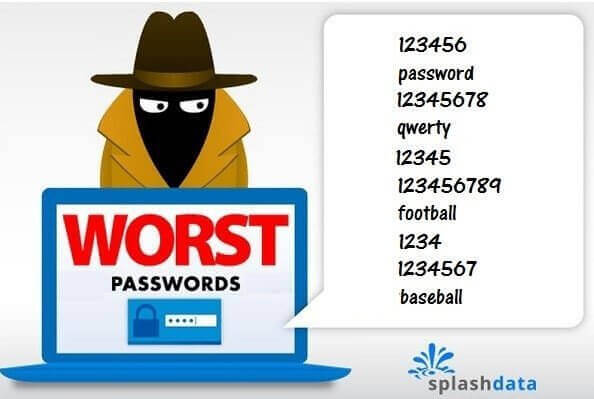
While becoming “123456” as your phrase is quite bad, the other phrases found on a list of Top 100 Worst Passwords of 2017 are just as distressing and...
Relayer is an SMB relay Attack Script that automates all the necessary steps to scan for systems with SMB signing disabled and relaying authentication request...
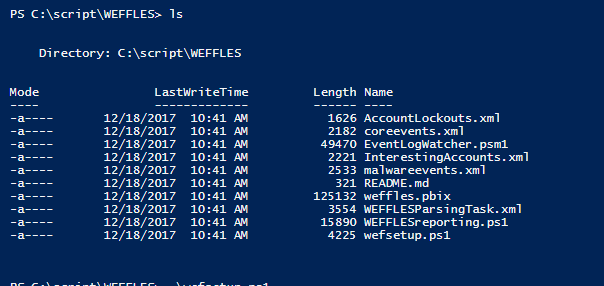
WEFFLES is designed to be small and lightweight, both for speed of getting something deployed during an Incident Response and also for the sake of being...
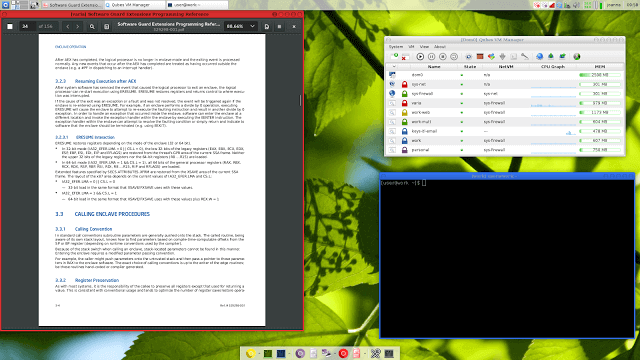
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
The administration of Guangzhou, center of the southern coastal province of Guangdong, began on Monday a pilot plan that creates a virtual ID card, which...
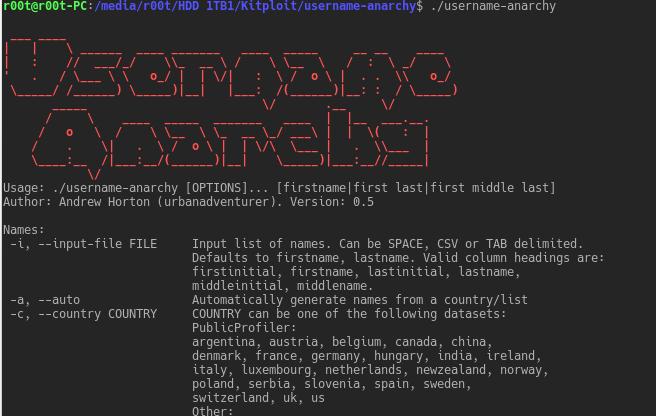
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...