[sc name=”ad_1″] A collection of cool tools used by Mobile hackers. Happy hacking , Happy bug-hunting Weapons OS Type Name Description All Analysis...
Search Results For - /Windows
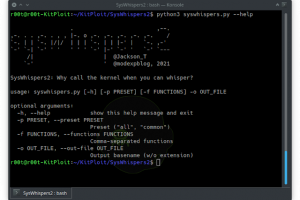
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
[sc name=”ad_1″] This is a tool that allows you to offensively use YARA to apply a filter to the events being reported by windows event logging...
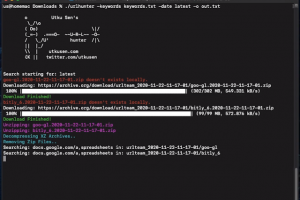
[sc name=”ad_1″] urlhunter is a recon tool that allows searching on URLs that are exposed via shortener services such as bit.ly and goo.gl. The...
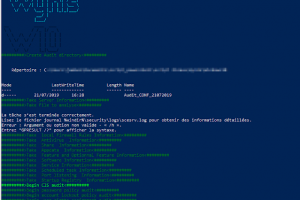
[sc name=”ad_1″] Just a powershell scripts for auditing security with CIS BEST Practices Windows 10 and Window Server 2016 You just need to run the...
[sc name=”ad_1″] A bento (弁当, bentō) is a single-portion take-out or home-packed meal of Japanese origin. Bento Toolkit is a simple and minimal...
[sc name=”ad_1″] Stegseek is a lightning fast steghide cracker that can be used to extract hidden data from files. It is built as a fork of the...
[sc name=”ad_1″] GUSTAVE is a fuzzing platform for embedded OS kernels. It is based on QEMU and AFL (and all of its forkserver siblings). It allows...
[sc name=”ad_1″] PYTMIPE (PYthon library for Token Manipulation and Impersonation for Privilege Escalation) is a Python 3 library for manipulating...
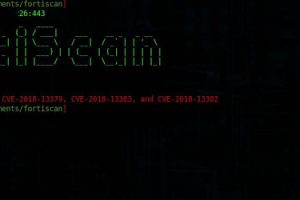
[sc name=”ad_1″] (CVE-2018-13379) Exploitation Tool, You can use this tool to check the vulnerability in your FortiGate SSL-VPN. ...