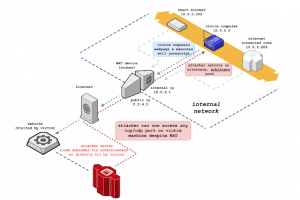
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
Search Results For - /Hidden
[sc name=”ad_1″] Automated Instagram Unfollower Bot. Installation : apt update apt install git curl -y git clone git://github.com/htr-tech/unfollow...
[sc name=”ad_1″] Tor is free and open-source software for enabling anonymous communication. The name derived from the acronym for the original...
[sc name=”ad_1″] This Module will hide files inside images ( currenlty PNG ) and export the modified image to disk The maximum size of file which...
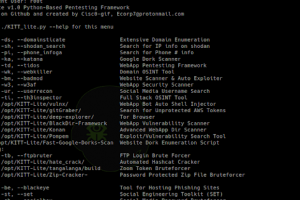
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...
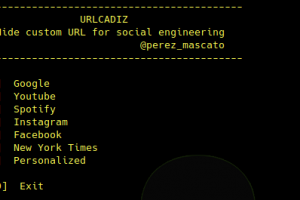
[sc name=”ad_1″] A simple script to generate a hidden url for social engineering. Legal disclaimer: Usage of URLCADIZ for attacking targets without...
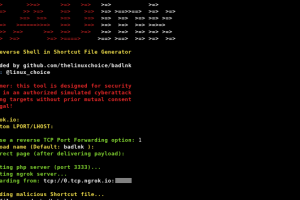
[sc name=”ad_1″] Reverse Shell in Shortcut File (.lnk) How it works? Shortcut file (Microsoft Windows 9.x) LNK is a file extension for a shortcut...
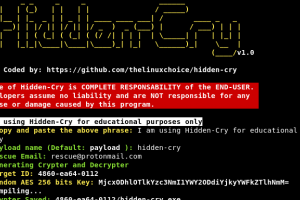
[sc name=”ad_1″] Windows Crypter/Decrypter Generator with AES 256 bits key Features: Works on WAN: Port Forwarding by Serveo.net Fully Undetectable...
[sc name=”ad_1″] FOCA (Fingerprinting Organizations with Collected Archives) FOCA is a tool used mainly to find metadata and hidden information in...
[sc name=”ad_1″] stegify is a simple command line tool capable of fully transparent hiding any file within an image. This technique is known as LSB...